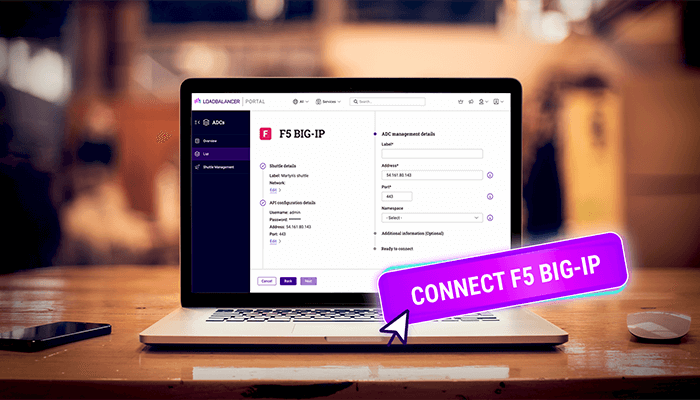
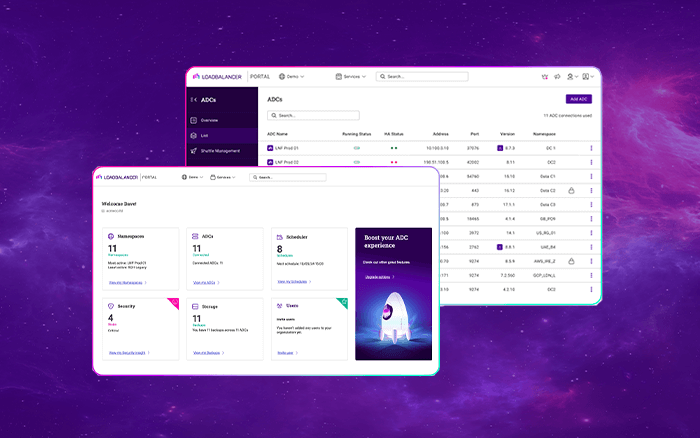
F5 / Citrix / Kemp
Compare and migrate from leading ADC vendors like F5, Citrix NetScaler, and Kemp. Get honest comparisons on features and cost, plus guides for seamless migration and managing your multi-vendor load balancer estate with our centralized ADC Portal.