One NetScaler engineer's take on using Loadbalancer's third-party centralized management platform, the ADC Portal, to manage their appliance.
What is the Loadbalancer ADC Portal?
When you have lots of NetScalers or a mix of third-party load balancers in your network, it can become quite cumbersome to update and back them all up.
Loadbalancer is aware of this and created the ADC Portal as a result. Their centralized management platform is designed to make backups and updates easier in complex environments. As a NetScaler specialist, they asked me to test the product and share my honest thoughts.
Here I document the process of setting up a NetScaler appliance in the ADC Portal, and report on my initial findings.
Setting up an ADC Portal account
You can easily set up a account, free for 90 days.
They have multiple account tiers, but the free trial comes with Business Tier features. Currently the third-party functionality is limited but includes:
- The ability to connect multiple load balancers (including NetScalers, F5s, and Kemp appliances, as well as Loadbalancer's own ADC)
- Unlimited Citrix NetScaler backups
- SSL certificate expiry monitoring
- Real-time CVE monitoring
- Secure Direct access
- Secure Remote access
The roadmap for 2025 includes:
- Citrix NetScaler updates
The setup is very easy. You can navigate to the ADC Portal home page, click the 'Create account' link and enter your details:
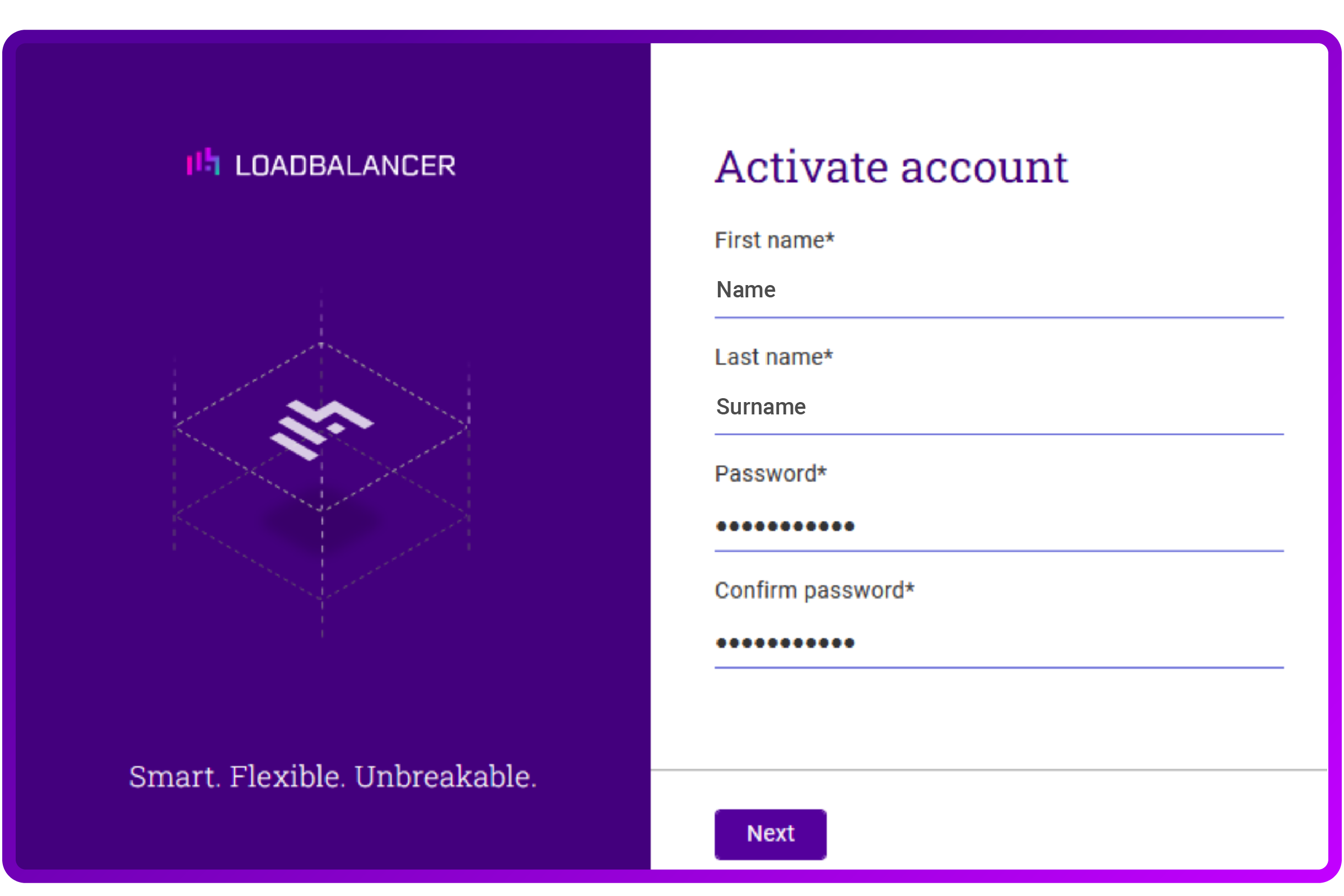
If you do require some additional guidance, they document the process very neatly in their Manual.
After entering the details of your account, the screen presents you with a unique lbUserPrivate.key.
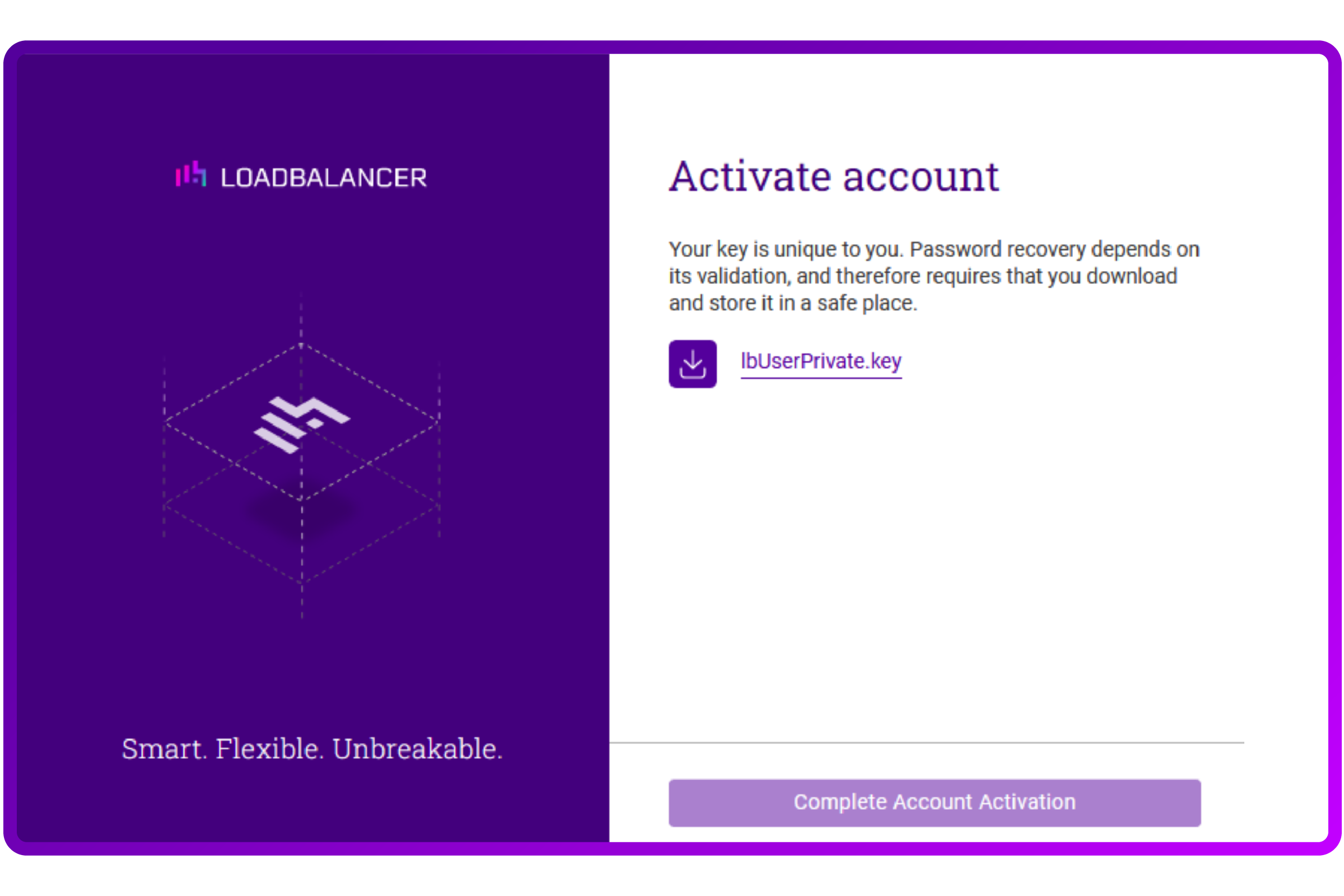
You might wonder why they chose an approach like this, but the answer is simple; everything is encrypted.
Upon creating your 'Organization' (the next step in the account creation process), you will also be presented with a lbOrgPrivate.key.
Everything you do in the ADC Portal is encrypted using these keys as they take security very seriously. As such, if you lose they keys, Loadbalancer is not able to help you. So be sure to save the keys in a secure place, you might need them someday; you have been warned!
How I added my Citrix NetScalers to the ADC Portal
While the product is capable of managing multiple ADC products at once (NetScaler, F5, Kemp etc.) my interest is only in managing NetScaler appliances.
Step One: Deploy the sidecar agent
To manage one or multiple devices in a network, we need to deploy a sidecar agent that Loadbalancer calls the Shuttle.
This is a proxy that Loadbalancer has developed for streamlining communication. I like this, as it allows for more elaborate setups with DMZ’s for increased security.
- Log into the ADC Portal at https://portal.loadbalancer.org:
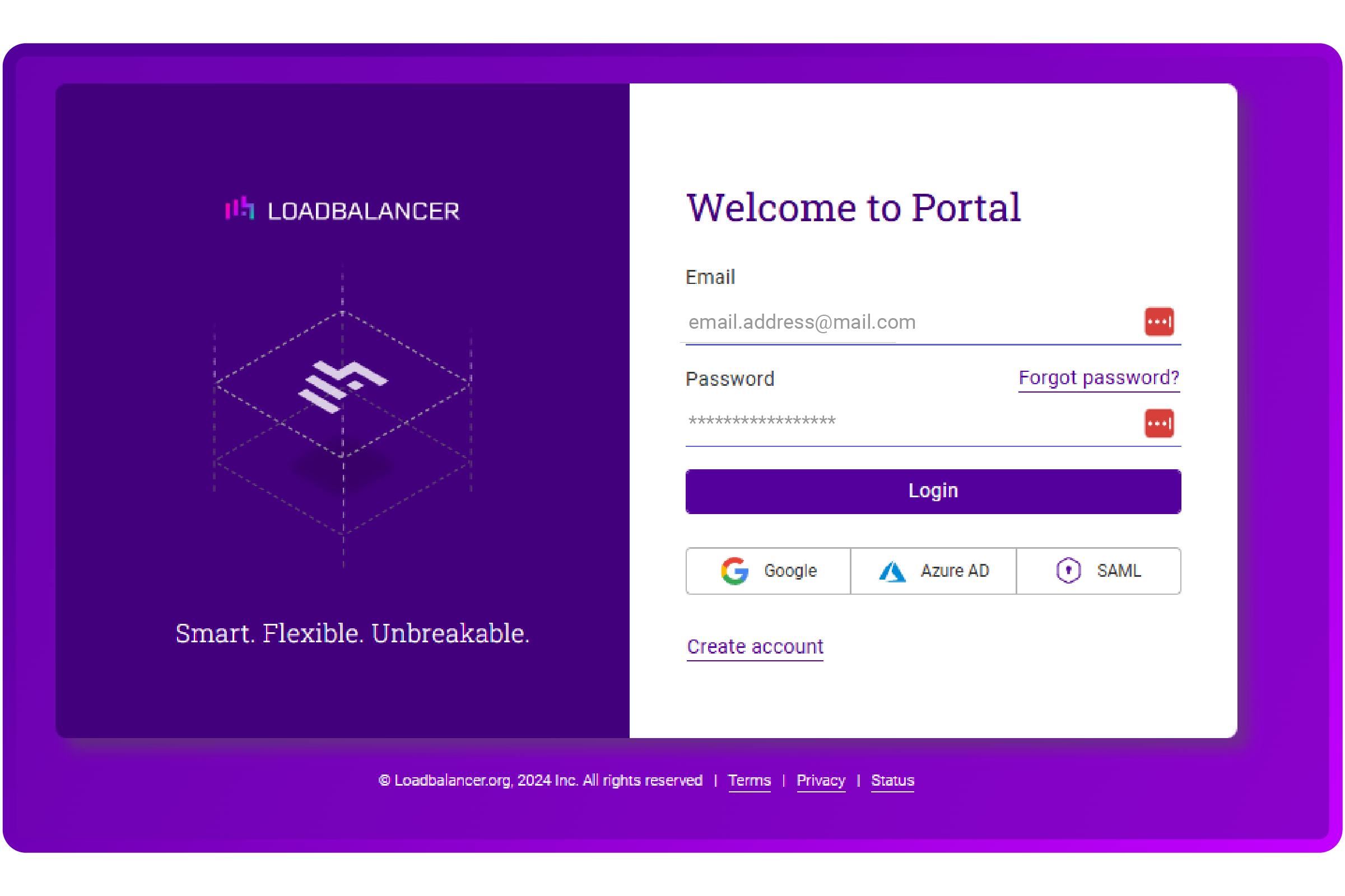
- On the Dashboard, click 'Connect an ADC':
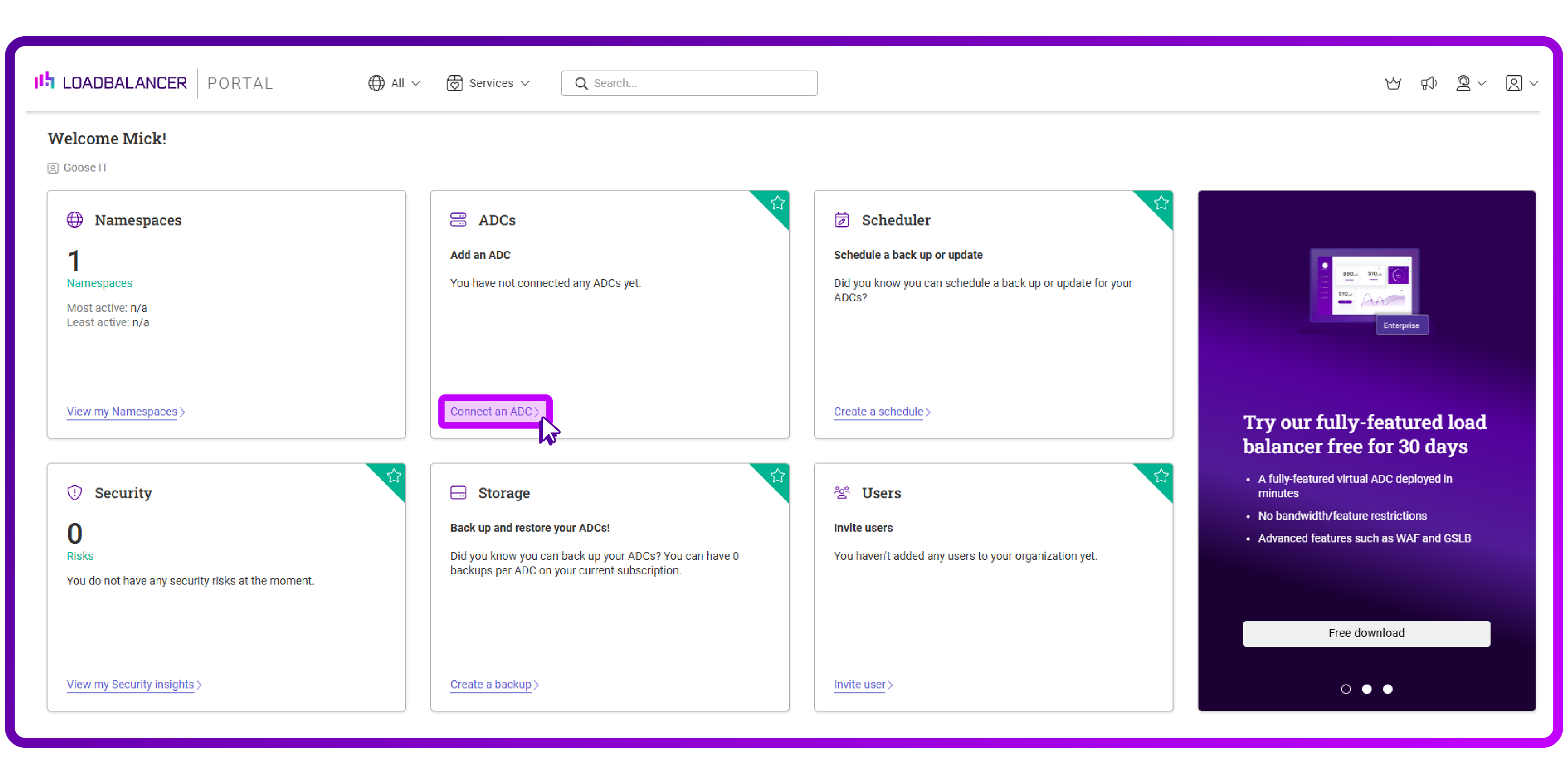
- Click on 'Shuttle Management':
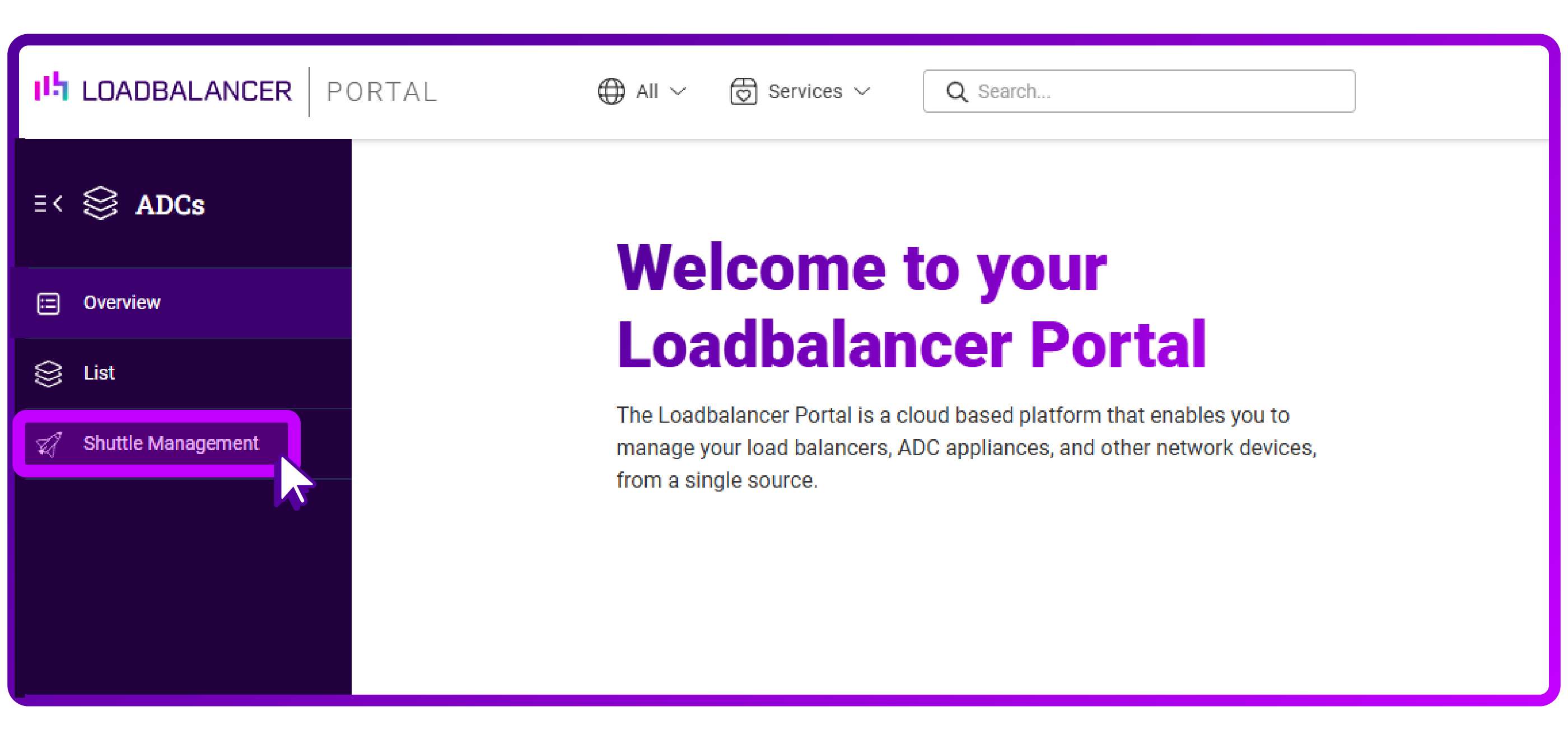
- I want the 'Standalone Shuttle' so I 'Add' that one:
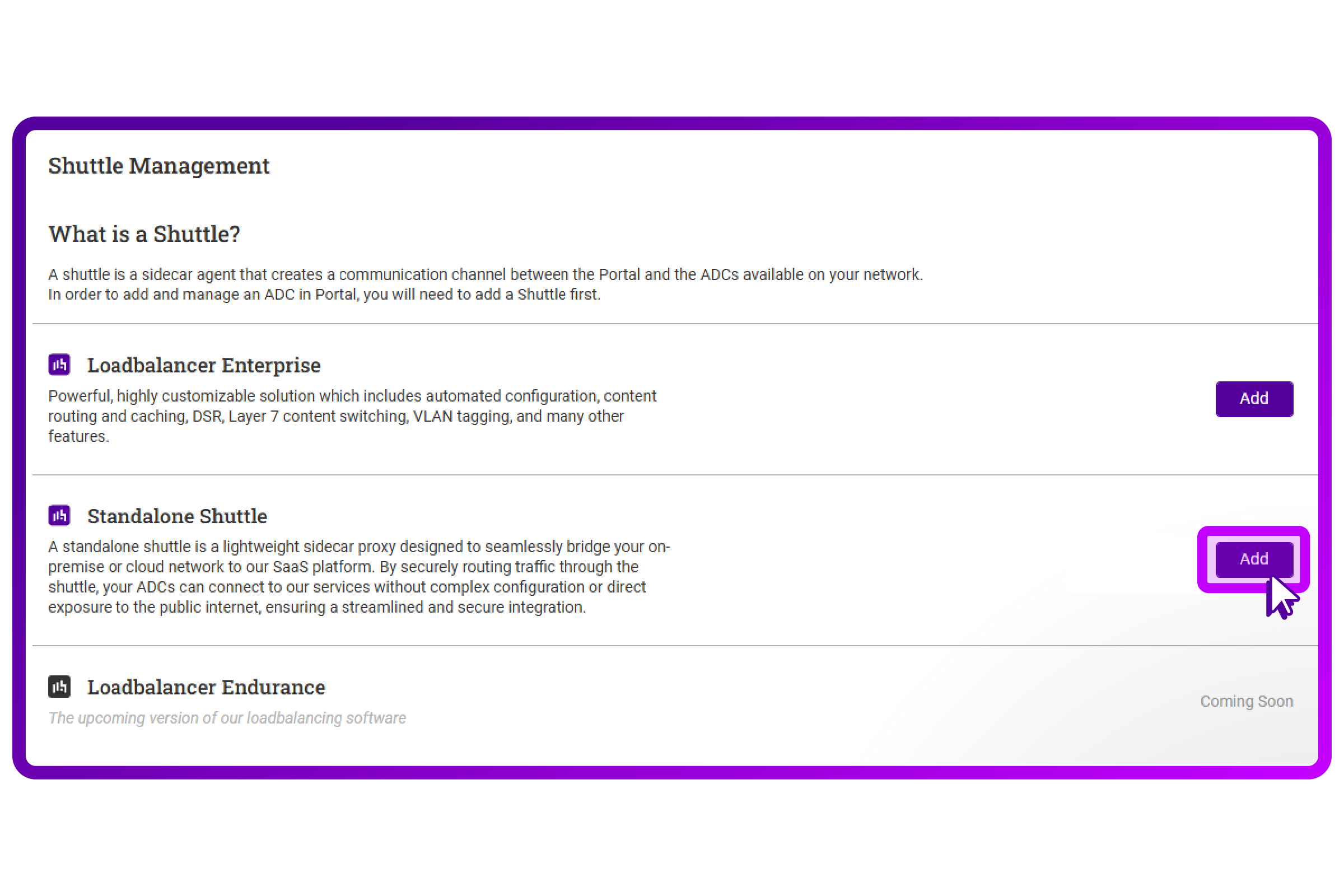
- The screen presents me with some information on how to setup the Shuttle. It appears to be working through a token mechanic with a simple install command. This is user friendly, but it does require an internet connection towards https://lbshuttle.sh:
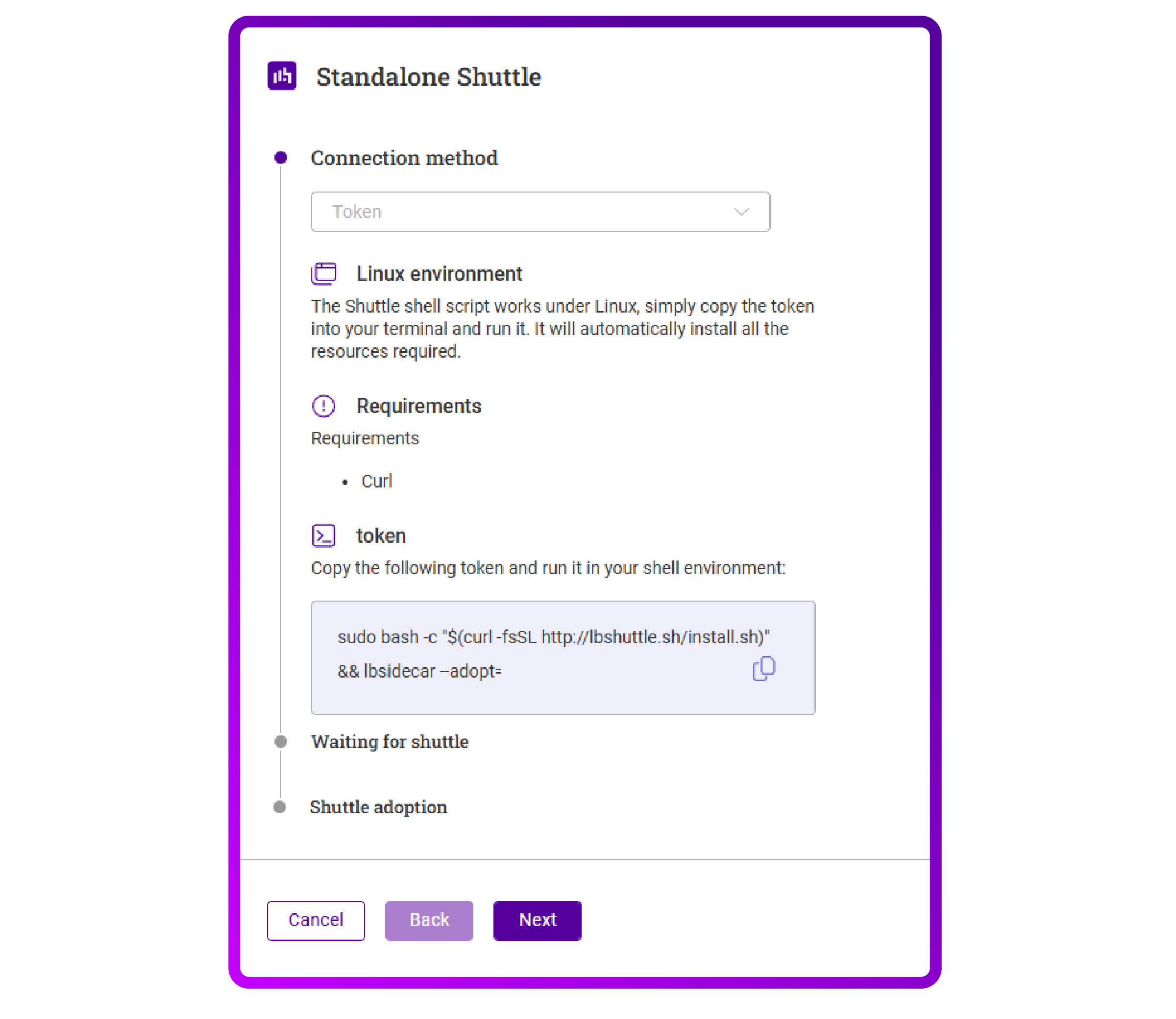
- I copied the command and deployed it in my lab Ubuntu VM running:
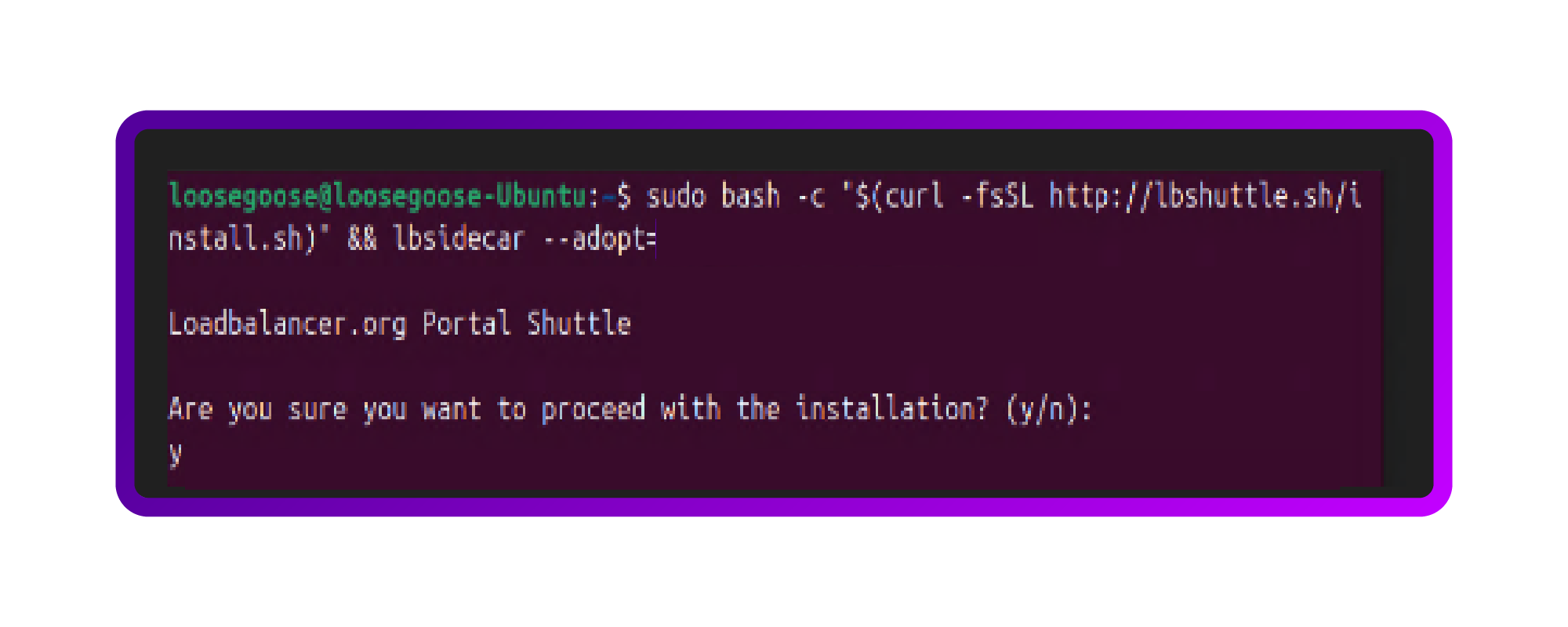
- After pressing “y” and “enter” it presents me with the following message so I then continue in the ADC Portal:
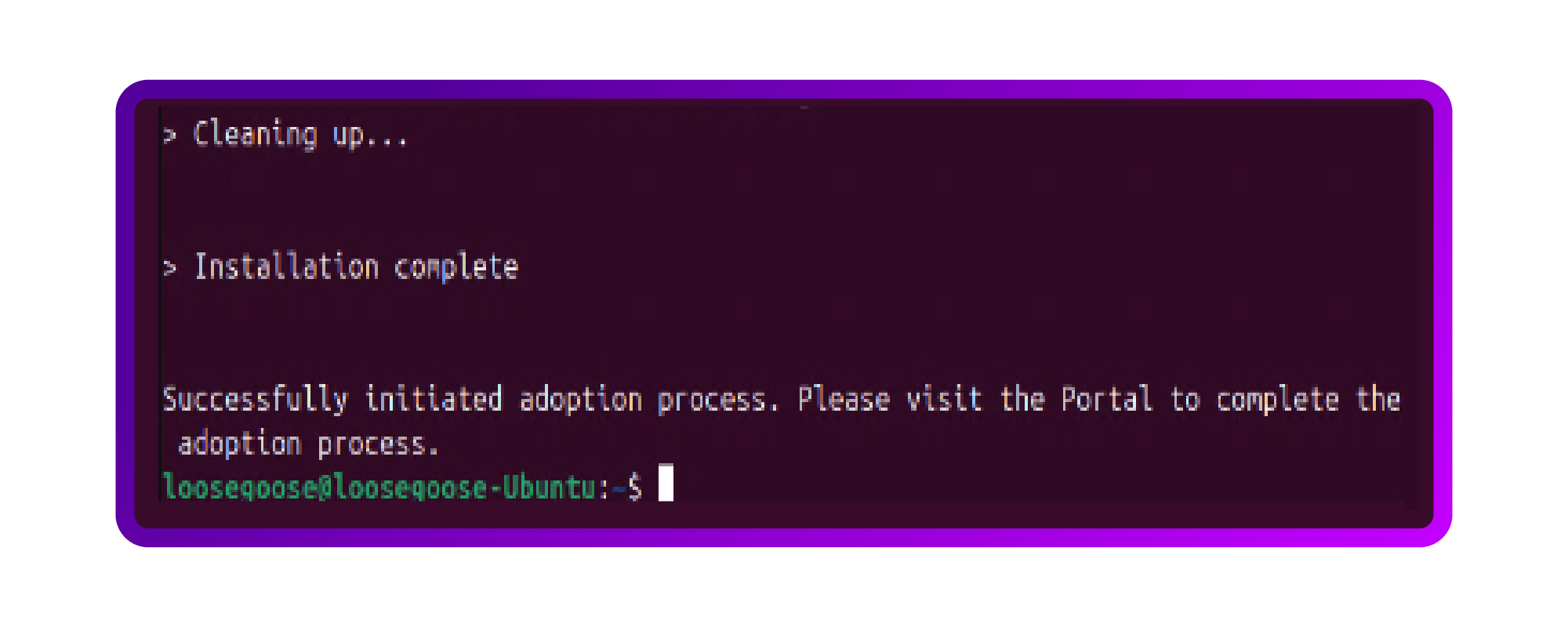
- The ADC Portal now shows me a new Shuttle, the Atlantis Expeditioner II. Excited, I press 'Adopt':
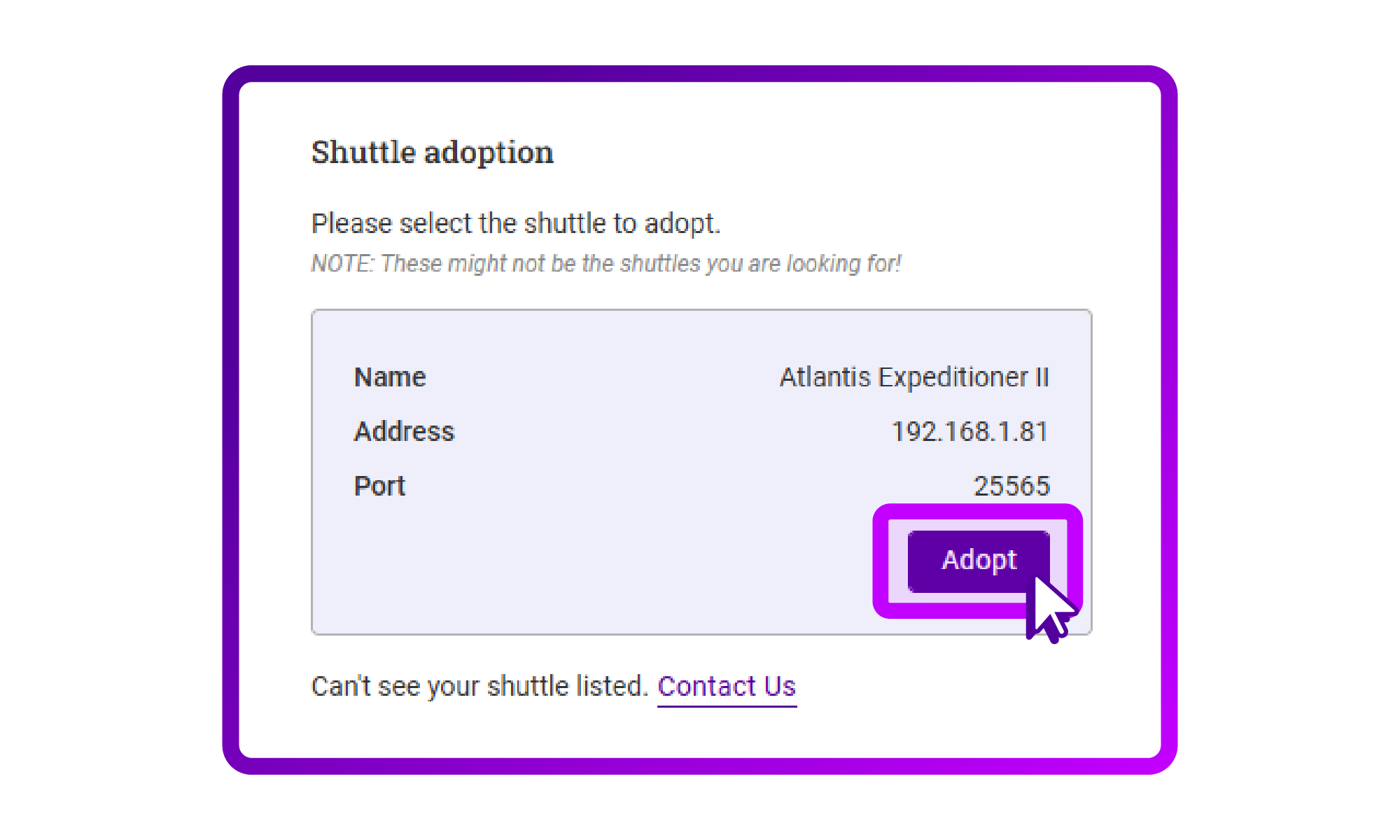
- I am then presented with the overview of my Shuttle(s). I can see that there are options to add subnets to the Shuttle for enhanced security.
Step Two: Start adding NetScalers
I now want to add a NetScaler ADC.
- Click on 'List' on the sidebar:
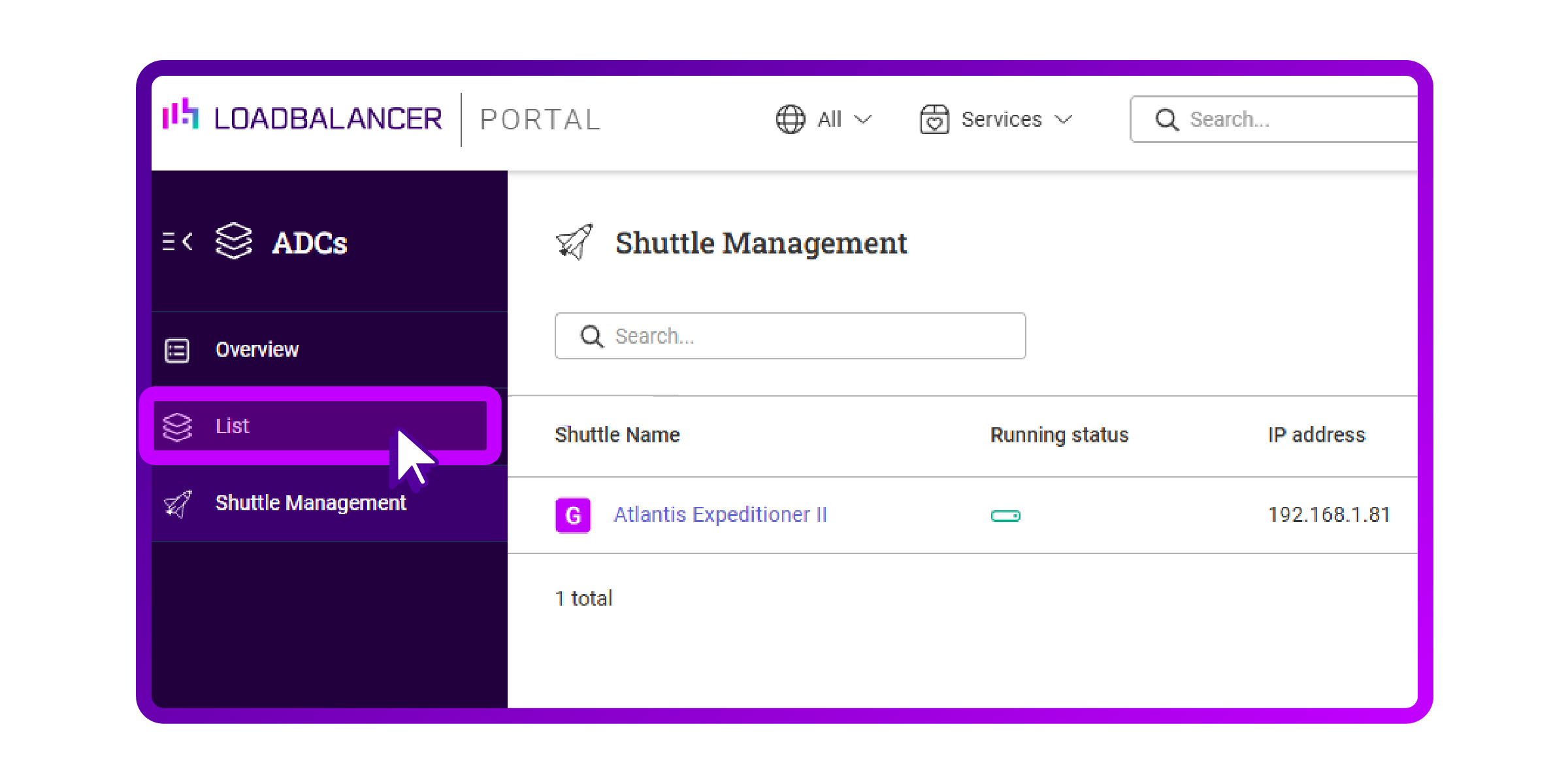
- Click on 'Add an ADC':
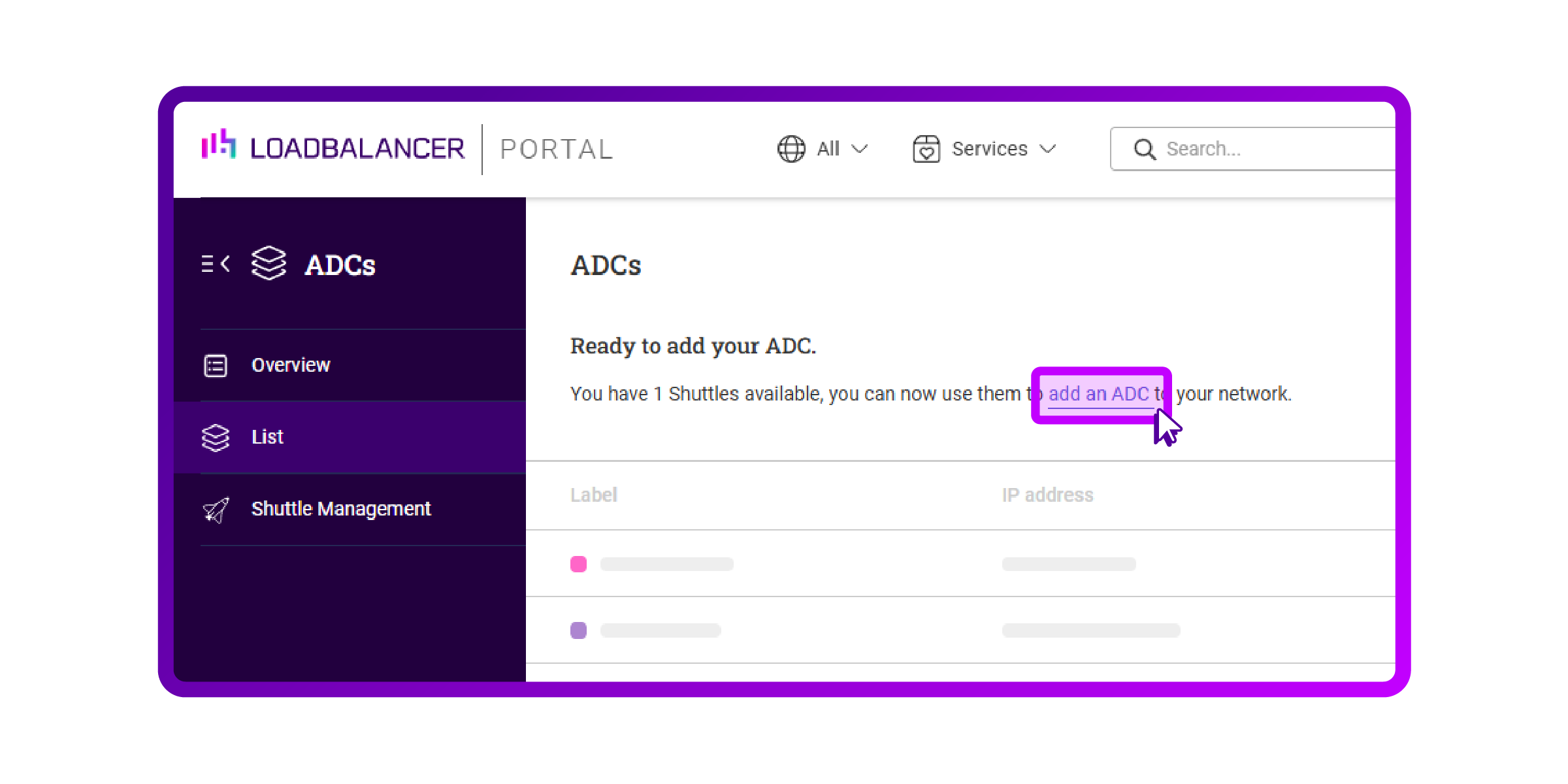
- Select the 'Citrix ADC' option and click 'Add':

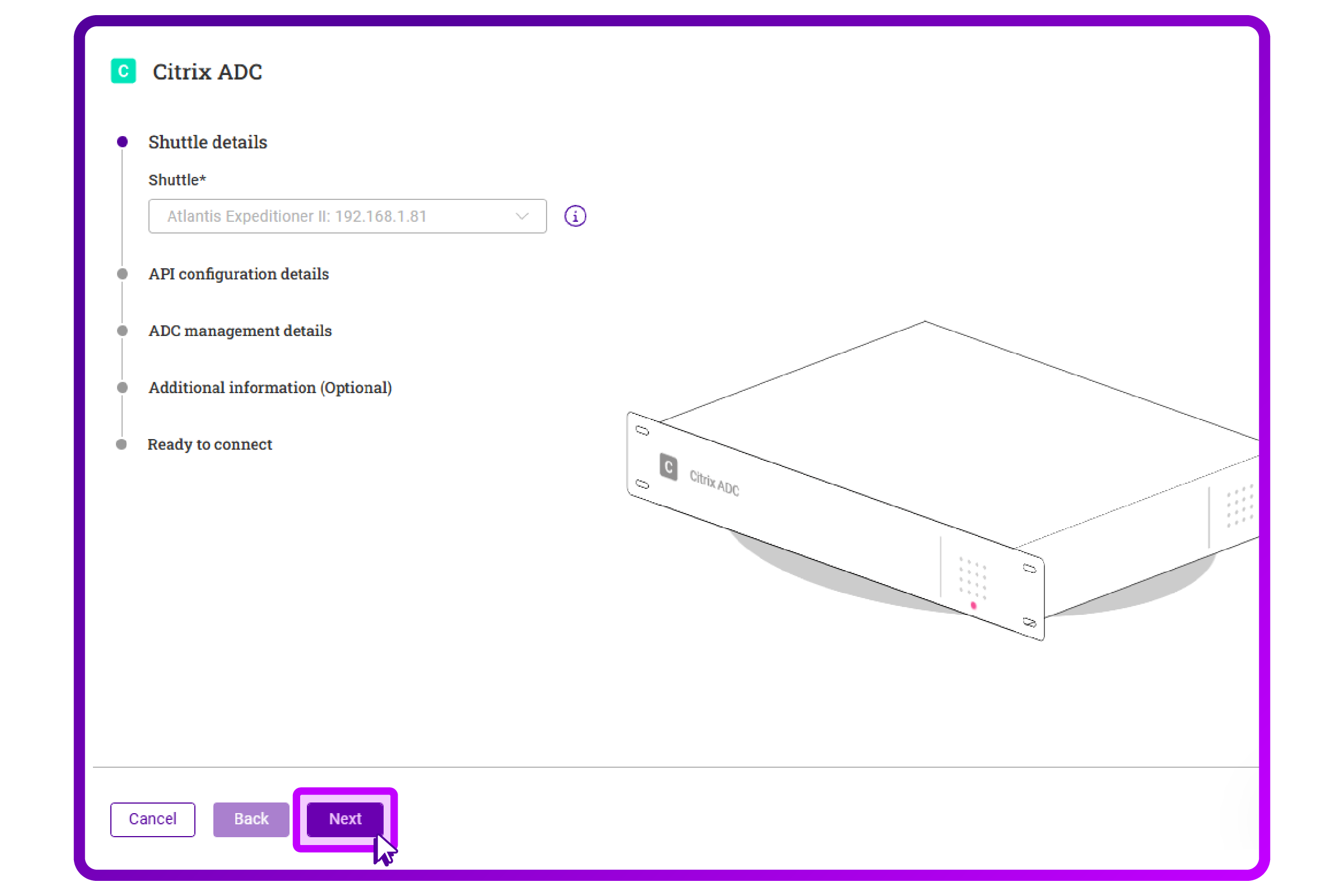
- Click 'Next':
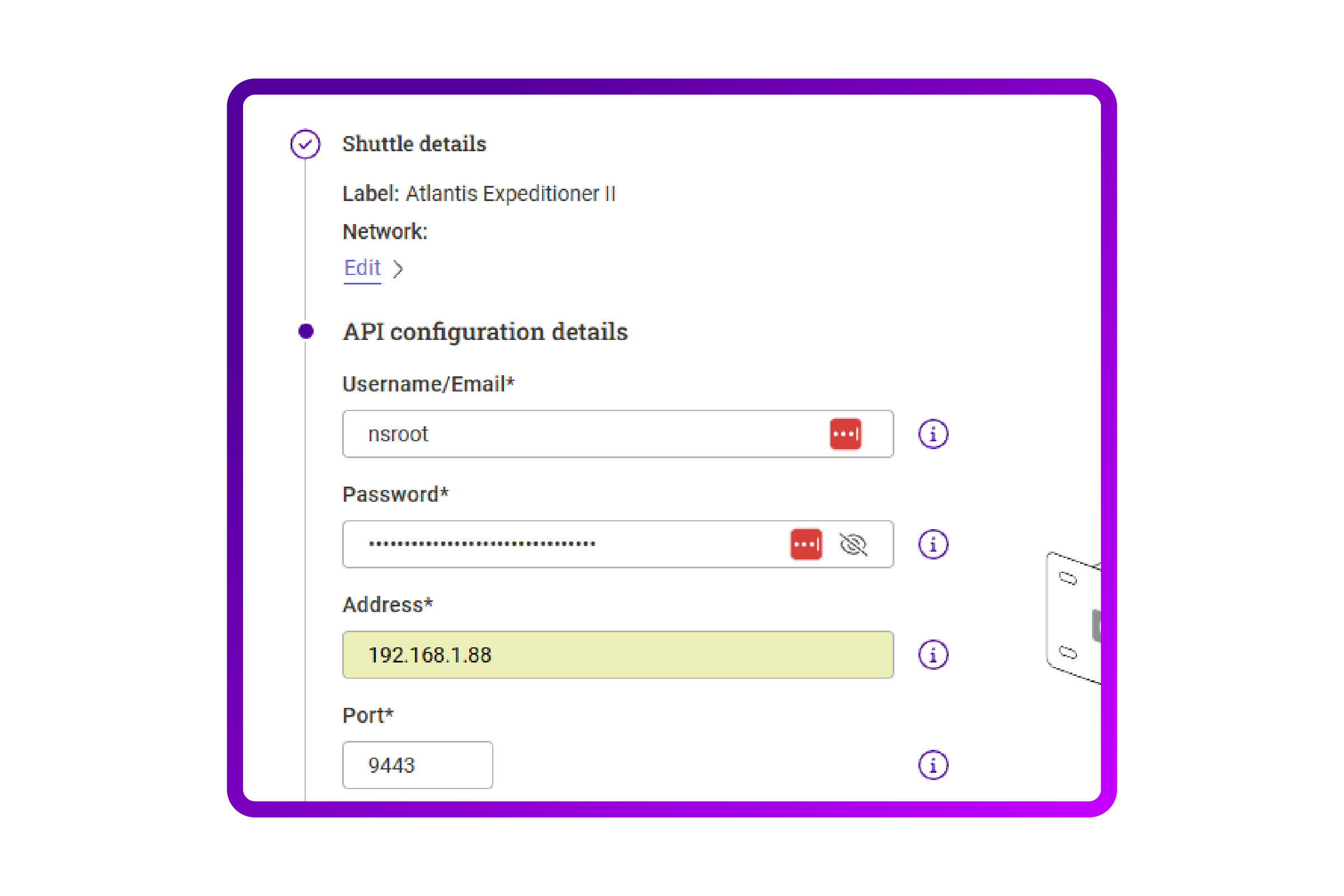
- I need to supply an account that has API access. My nsroot access should do.
I use port 9443 as I deployed a containerized NetScaler (CPX). Normally 443 is the way to go:
- I then do the same for the other management details:
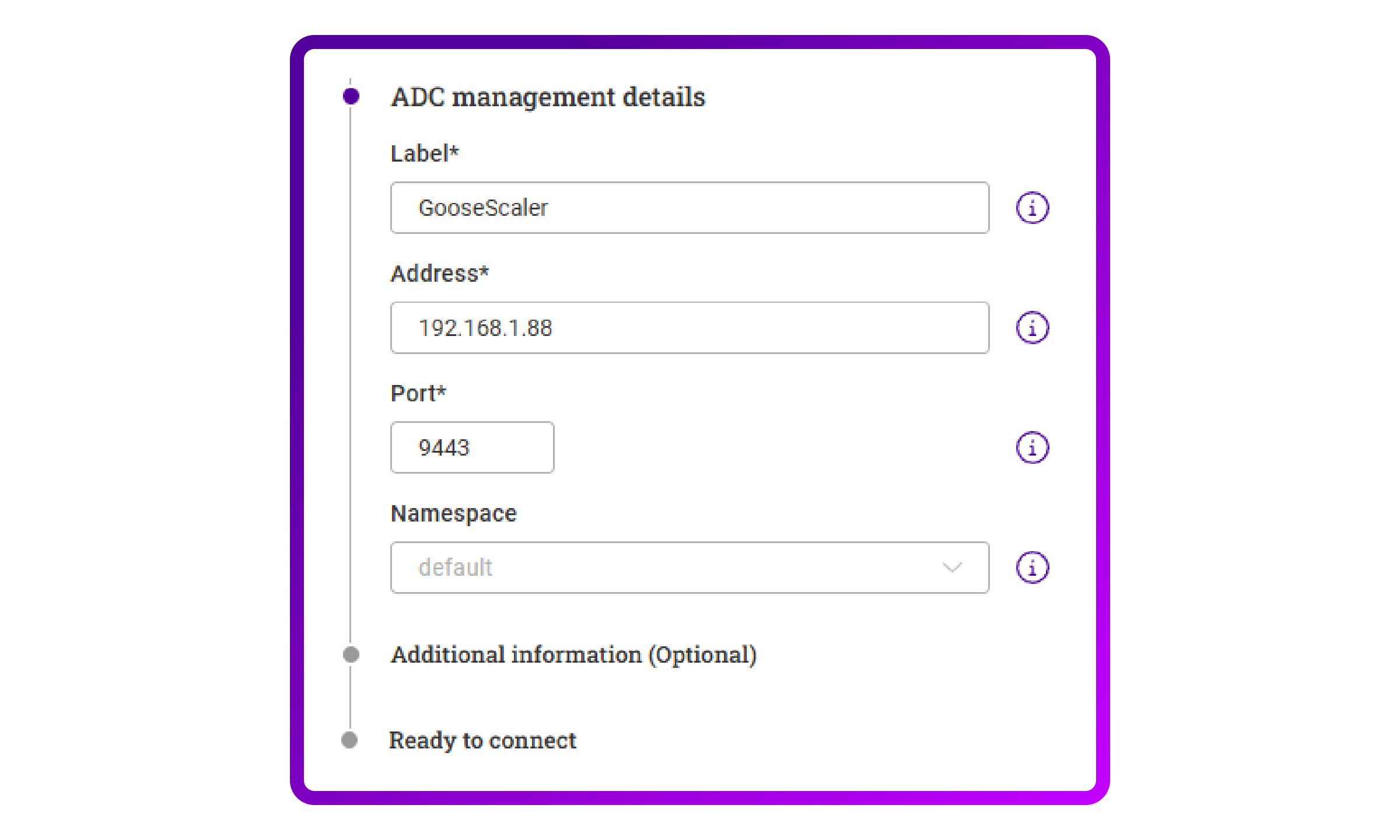
- After entering all the details I am now ready to submit.
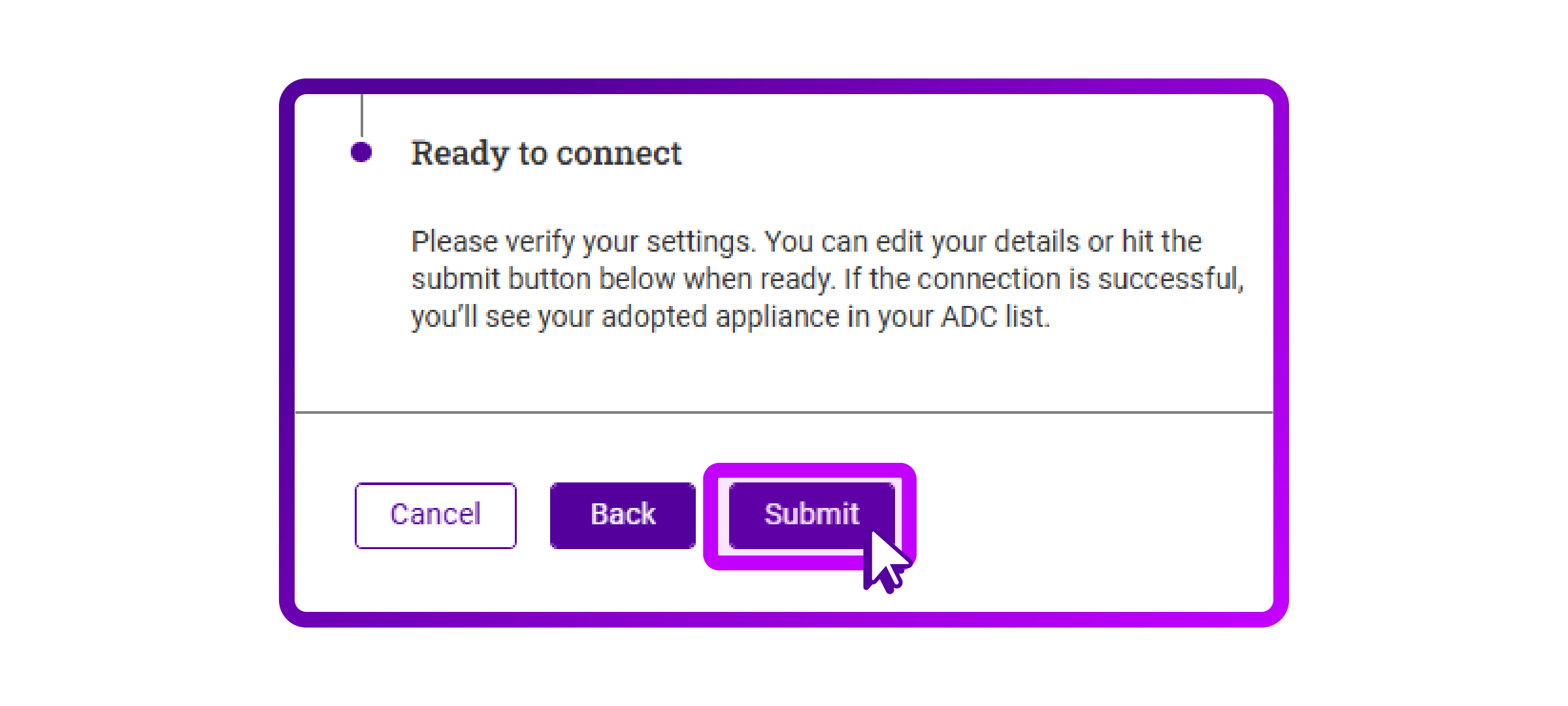
- I see that the NetScaler is now added:
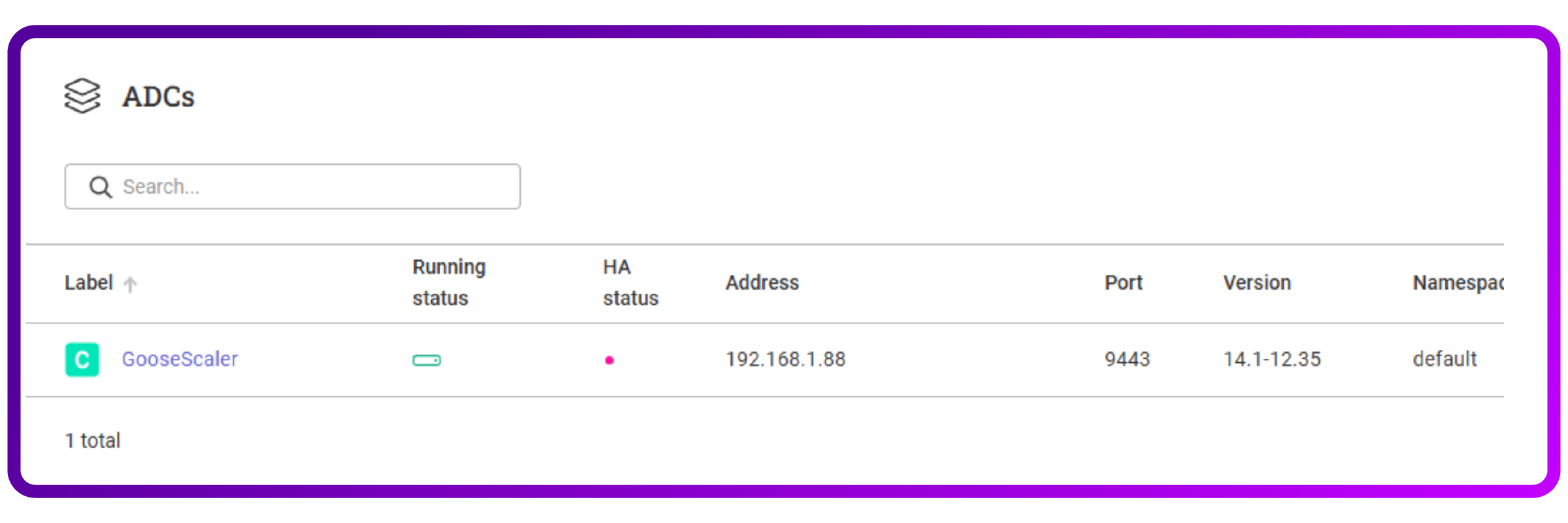
Mission accomplished! Now I'm up and running, here's what I actually did in the ADC Portal.
How I managed my Citrix NetScalers in the ADC Portal
Now that my NetScaler is added, let’s try using some of the available features.
Secure remote access
- When clicking on my NetScaler, I get the option to 'Warp to ADC':
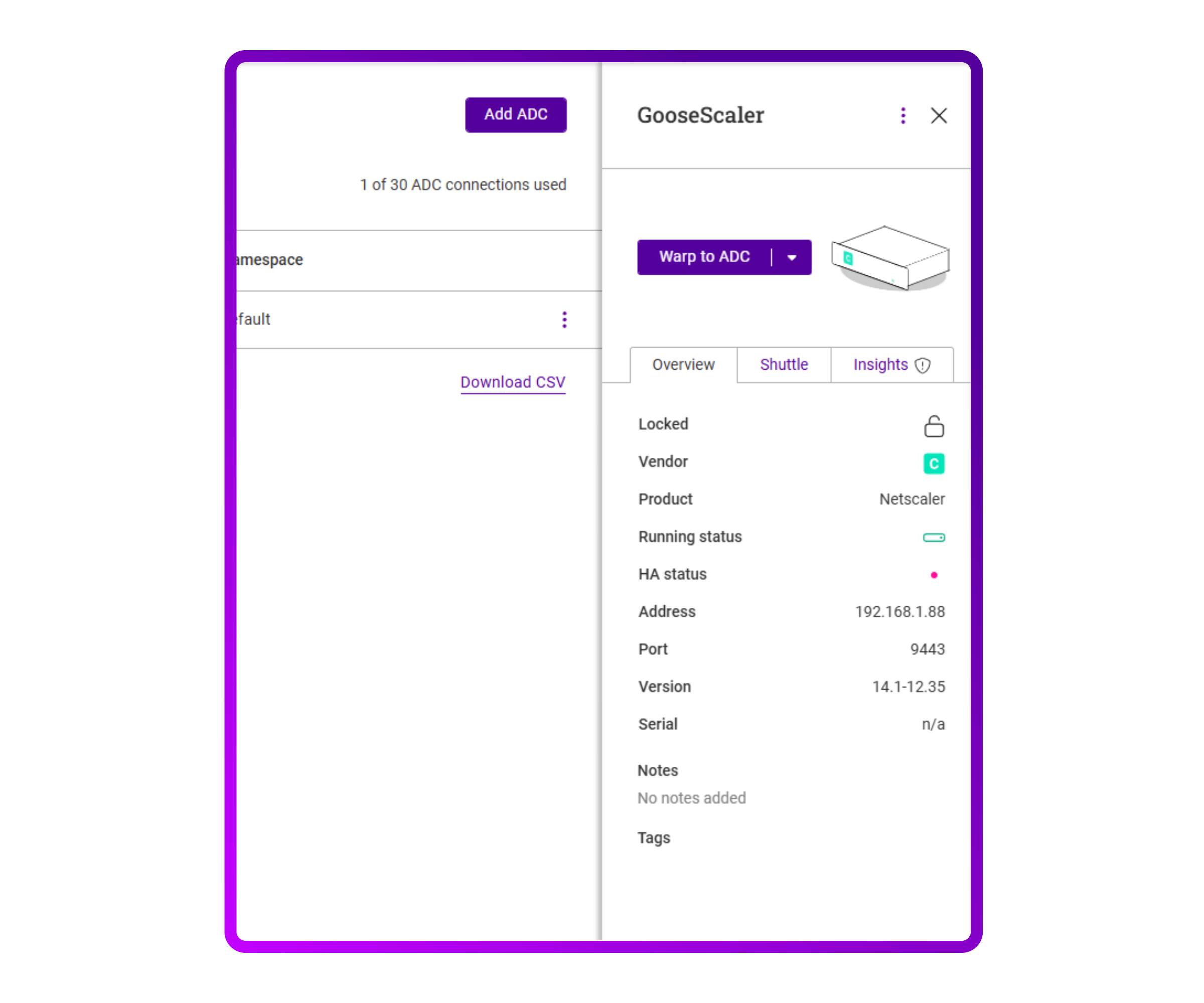
- After clicking on it I get presented with a login screen and it works as usual. This is a neat VPN-esque solution for allowing centralized management. The response of the Warped session is very slow, but that might be because my NeScaler has limited resources.
Backing up my NetScaler
- The backups are also centrally managed from the overview.
- I can manually create one by clicking the three dots on the right side of the entry:
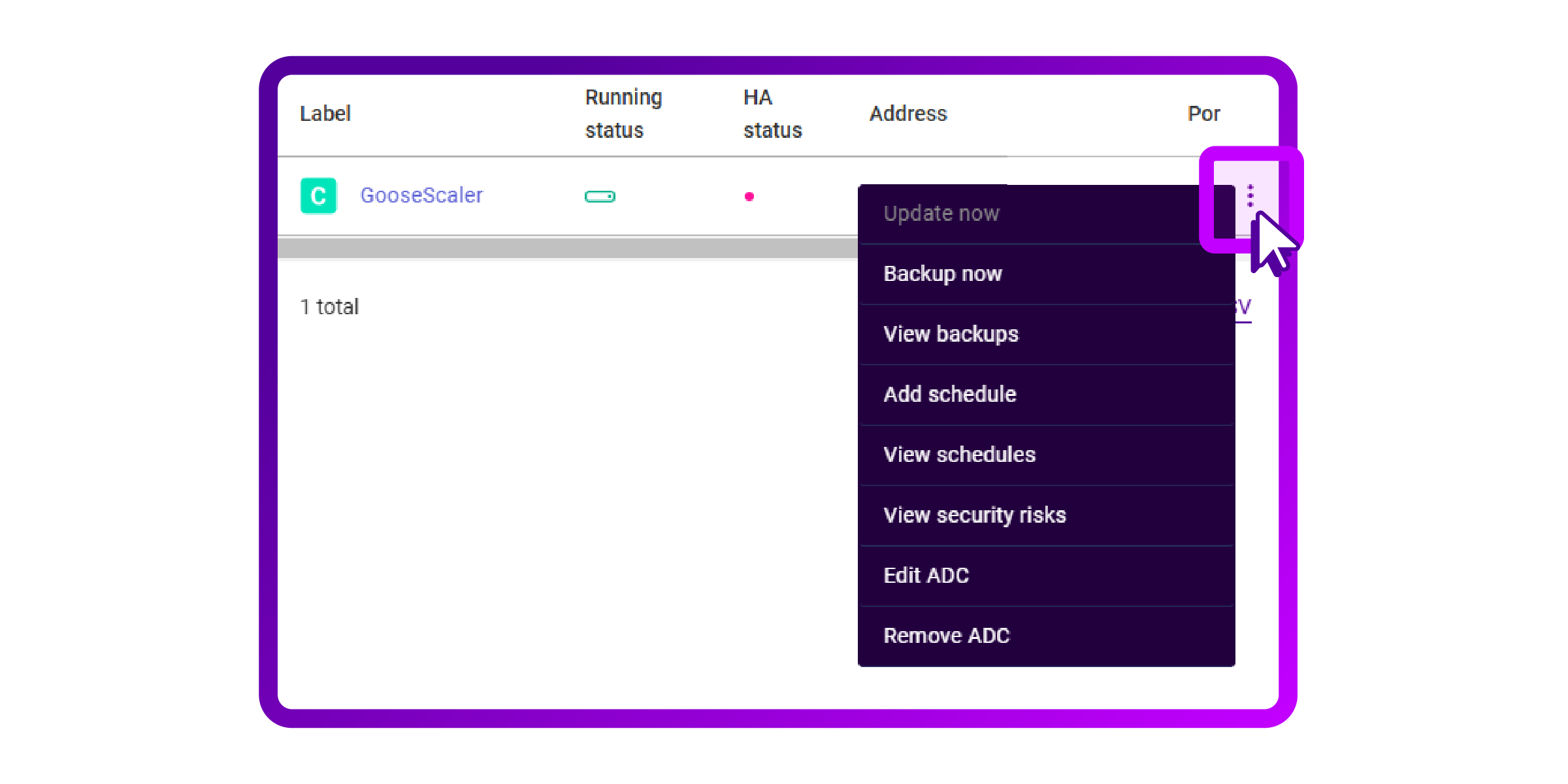
- After clicking 'Backup now' I get a toast notification telling me “Success!”.
- A small cloud icon with an arrow in it is now presented in my entry. I assume this means the backup is in progress:
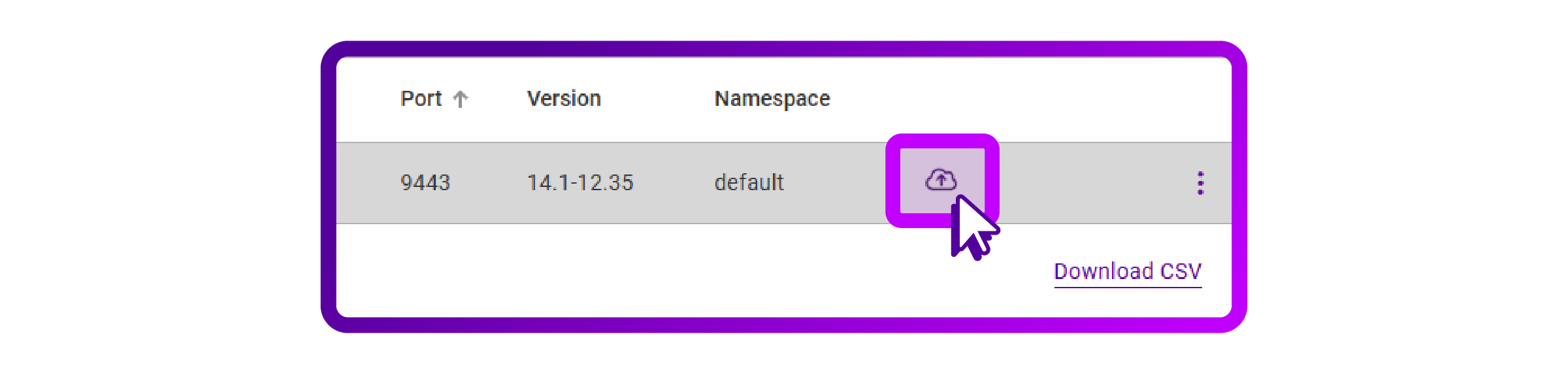
- While pondering over the meaning of the icon, I wondered if I could automatically backup my NetScaler. You can!
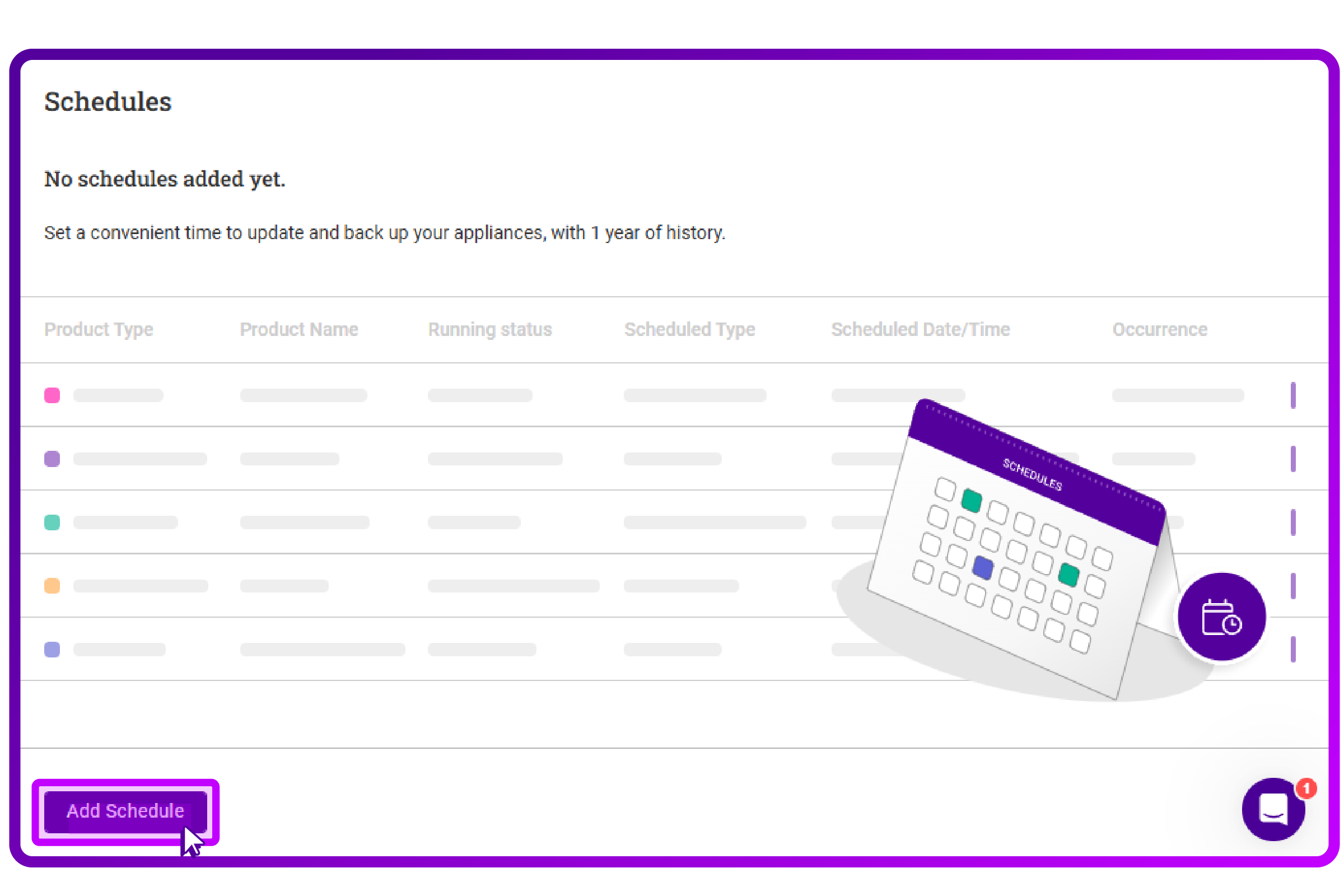
- If you press the three dots again, you also see 'View schedules' as an option.
Pressing it brings you to the schedule screen, where I click on 'Add Schedule':
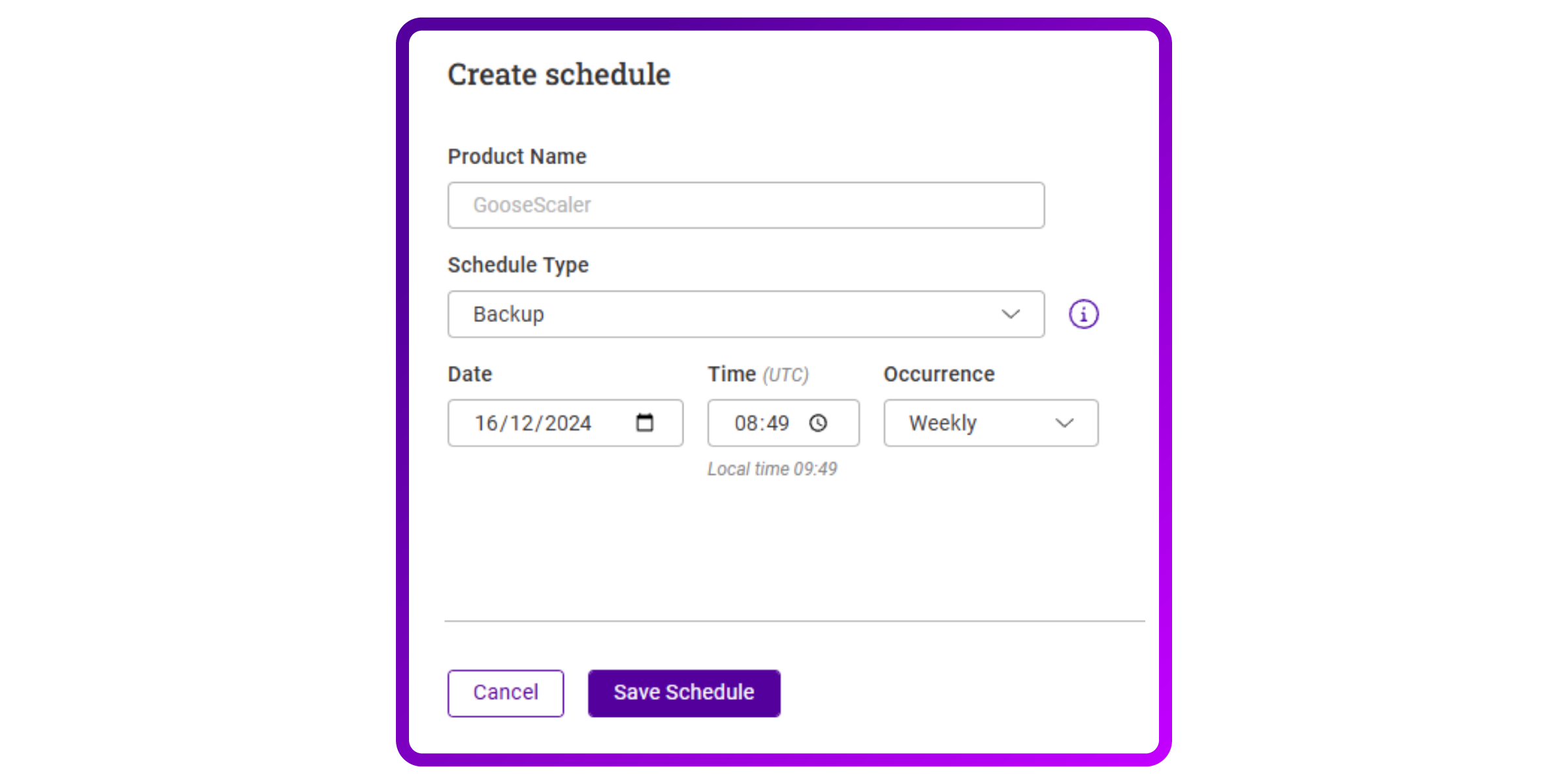
- I just needed to select an occurrence, and that’s it. I like this. It doesn't need to be more complex, although it would be nice to be able to choose Basic or Full backup types. I asked, and currently the backups are Full by default:
- After saving, I’m presented with a neat overview:
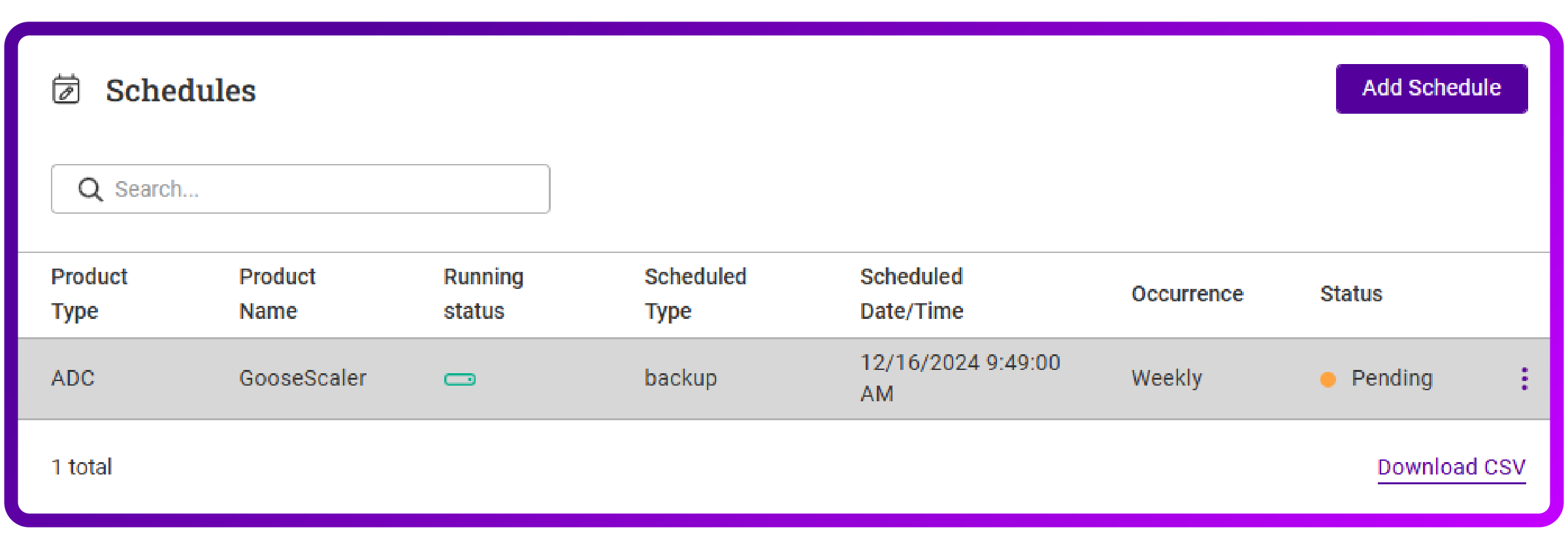
Job done.
Security insights
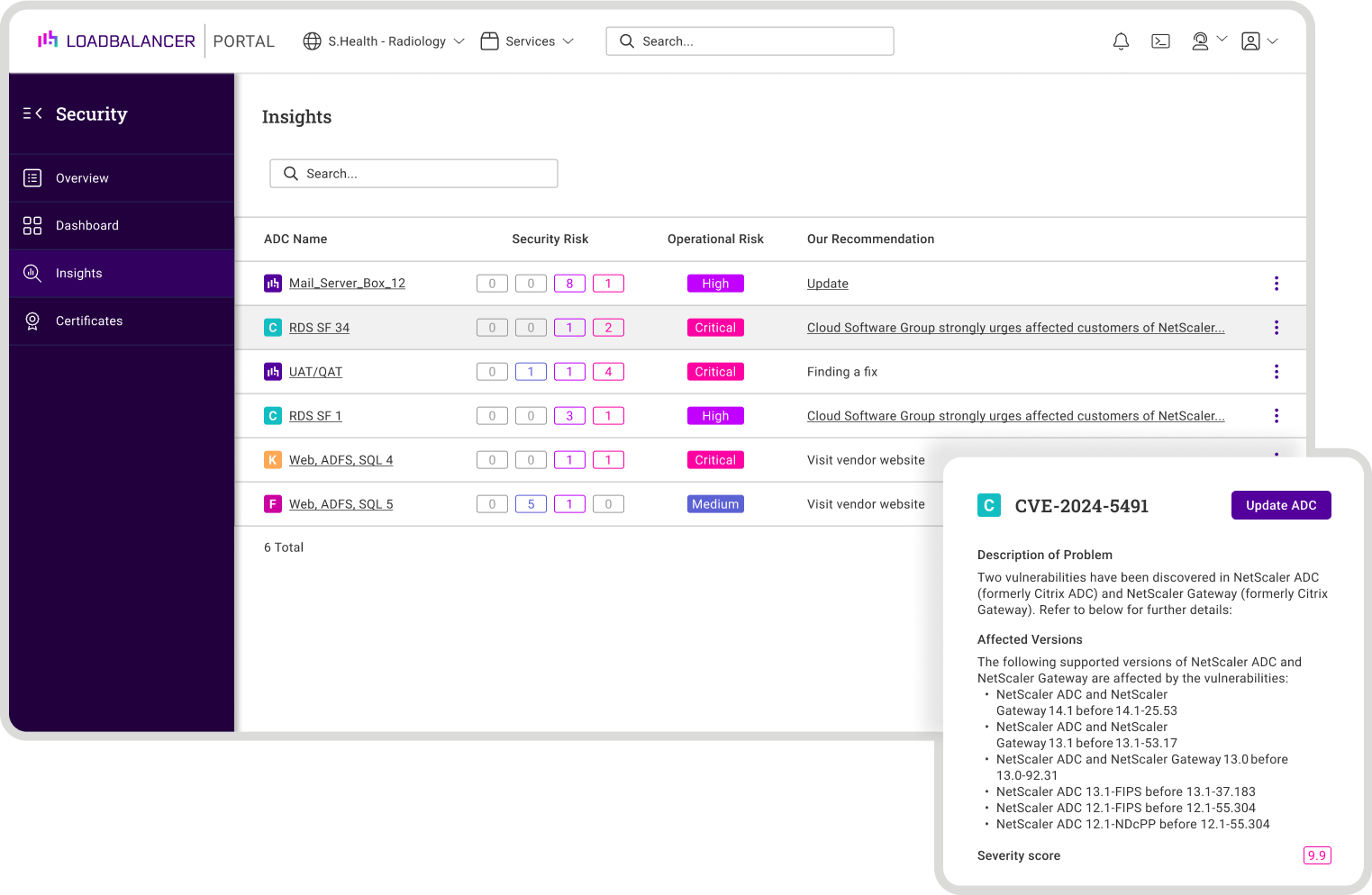
One of the other neat features in the ADC Portal is it's ability to provide a comprehensive overview of CVE’s currently detected on your configuration(s).
What I like about this, is that normally vendor solutions focus only on their own vulnerabilities, but this shows any third-party CVE in real-time.
These security insights therefore provide information on all your connected ADC devices.
It also has a button that allows you to export to CSV so you can easily distribute work to the appropriate teams.
Additionally the CSV files also allows for interesting automation opportunities if you are skilled with PowerShell.
My NetScaler didn't have any CVEs so I wasn't able to replicate an alert but here's what one might look like according to the product documentation:
Expired SSL certificates
It's also possible to monitor SSL certificates in the ADC Portal.
In the Security section, simply do the following:
- 'Click Certificates'
- Click on the individual load balancer you're interested in
- See any 'Expired' certificates highlighted in pink, with the expiry date and certificate name visible next to this
Again, my SSL certificates were all up to date but here's a screenshot of what it would look like:
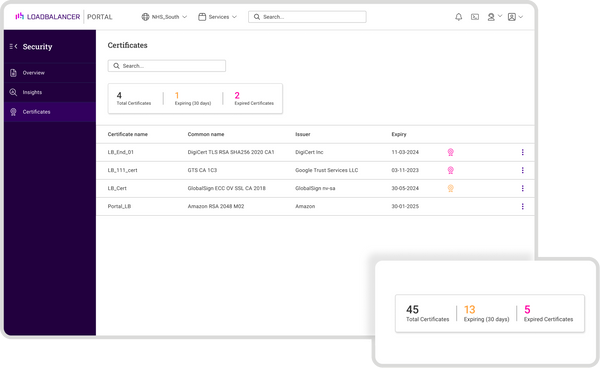
This is a nifty piece of functionality that makes tracking your certificates and expiry certificates a LOT easier.
Overall thoughts
The features presented by Loadbalancer ADC Portal are basic but easy to use. I find the setup straightforward enough and I appreciate the concern for security with features like subnets applicable to the Shuttle.
I believe the ADC Portal is a great tool for companies with one or more ADC solution that requires a comprehensive overview, while maintaining simplicity at its core.
In my opinion, the WARP functionality added the most value. For example, if you have multiple remote sites it is extremely beneficial to be able to access your NetScalers from a single, centralized console, while also being able to manage your other ADC appliances like F5.
If you combine this with the CVE vulnerability detection available, I can see how it would help reduce your response time to threats.
Overall the setup was a breeze in terms of technical complexity, just a bit of work to reproduce in a lab, but the experience is very user minded.
I would wager a junior engineer could easily manage to set this up. The interactions I had with the people over at Loadbalancer make it feel like a warm place; the type of company where people are happy to help and easily available.
If you need to manage lots of load balancer appliances from a single, centralized platform, I'd recommend giving it a go.
















