
How many engineers does it take to renew an SSL/TLS certificate? Several, you might joke. But you may not be far wrong!
SSL/TLS certification is a necessary but tedious and repetitive process that involves numerous steps and (depending on the size and complexity of your organization) could require input or collaboration from individuals across IT, Security, and DevOps teams.
Here I explain not just how to renew SSL/TLS certificates with Let's Encrypt, but also how to automate the process using our Enterprise ADC load balancer. Saving you time, and making everyone's lives a whole lot easier...

Why is TLS more important than ever in 2024?
TLS (Transport Security Layer) is a crucial protocol for the modern Internet. We have been told this for many, many years. Every major website in the world uses it and so should you. But in 2024 it's more important than ever. Here's why:
1. You need it to encrypt the connections between the client and server.
Imagine your address, credit card details and first pet’s name being sent over an unencrypted connection. Easy picking for the bad actors sniffing your traffic.
2. Search engines like Google prioritize secure websites in their rankings.
So, if your website doesn’t provide encryption, you will quickly find yourself on page 99 of the search results.
3. The lock icon has gone AWOL
Last but not least, do you remember the little green padlock displayed in browsers? It is gone! Why you ask? Because a secure connection is no longer optional, it’s a must! And the way the browser evolution goes, soon you may not even be able to connect to unencrypted websites.
Why Let's Encrypt is a SysAdmin's best friend
Let's Encrypt is a free, automated, and open source Certificate Authority (CA) for encryption that has revolutionized the way we renew certificates with the ACME (Automatic Certificate Management Environment) protocol. It is trusted by all major root programs, including Google, Microsoft, Apple, Mozilla and Oracle.
With Let's Encrypt, you can obtain, renew, and manage SSL/TLS certificates to secure your HTTPS connections, and while some were sceptical when it launched back in 2015 (Malcolm Turnbull, I’m looking at you lol...) Let's Encrypt has since then most definitely made our lives a whole lot easier.
All you need to do is configure your chosen software (acme.sh, certbot, dehydrated etc) to make obtaining and managing TLS certificates a breeze.
Here's how...
Automating SSL/TLS certificate renewal
The beauty of Let's Encrypt is that you can also set it up to automatically renew TLS certificates. While Let's Encrypt improves certificate issuing, manual renewals can be time-consuming and error-prone. The good news is that...
...by automating the renewal process with your Loadbalancer.org ADC, you can ensure your website's TLS security remains uninterrupted. So once you've set it up correctly, you can forget about it!
But how does it work, you might ask? Below, I'll walk you through each step to configure your Loadbalancer.org appliance to effortlessly automate TLS certificate renewal using Let's Encrypt.
So dive in, and follow these measures to provide your website visitors with a secure and stress-free online experience.
Let's Encrypt pre-requisites
Here's what you need to have setup on your load balancer, before you get started. Please note, the following procedure applies to Enterprise v8.11.1 or higher. For more help, check out our Admin Manual.
1. Create a backend-only VIP
- Navigate to Cluster configuration and then Layer 7 virtual services.
- Click Add a new virtual service.
- On the new page, click the Advanced options on the right and check the box next to Create backend only.
- You'll notice the backend doesn't have an IP address, but a label instead. Enter a descriptive label of your choice (i.e. letsencrypt) and click Create or Update.
- Once saved, click Modify next to your newly created virtual service.
2. Disable health checks
- On the modify page, scroll down to the Health checks section.
- Change the setting to No checks, always on.
- Scroll further down and click Update.
3. Add a Real Server
- Head to Layer 7 real servers in the side menu.
- Click Add a new real server next to your virtual service name.
- Enter the IP address 127.0.0.1 and set the port to 8888 (commonly used for Let's Encrypt HTTP challenges for ACME).
- Click Update to add the real server.
4. Configure your ACL rules
- Go back to Layer 7 virtual services and click Modify for the virtual service for which you want to issue the certificate.
- Scroll down to the ACL rules section.
- Click Add rule, select the type as Path beginning, and enter the specific URL provided by Let's Encrypt for the challenge. This URL will be displayed on their platform.
- Change the Action to Use backend and enter the label of the backend you created in step 1. Click OK.
- Finally, scroll down and click Update to save the changes.
- If you have more sites in need of a certificate, just repeat the same steps for each of them.
5. Add an SSL Termination
- Navigate to Cluster configuration and then SSL Termination.
- Click on Add New Virtual Service.
- In the Associated Virtual Service dropdown menu, select the name of the Layer 7 virtual service you want to secure with SSL.
- Click Update to save the configuration.
- Reload Stunnel and HAProxy
Further reading:
- The pros and cons of offloading TLS/SSL encryption and decryption to your ADC
- How to master SSL termination in HAProxy: considerations and configurations
- When is it right to SSL offload?
How to configure an Enterprise load balancer for Let's Encrypt
Now for the fun stuff...
Step One: Login
- Login to your Loadbalancer.org appliance via SSH using your preferred method.
Step Two: Enable lb-letsencrypt
- Using lb-letsencrypt.sh, install and upgrade the acme.sh script:
lb-letsencrypt.sh -u
- Open a ssh client to the Active load balancer and run the following command (use sudo if on AWS or Azure):
Process Stunnel is running, continuing.
We do not have a Secondary node
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1032 0 1032 0 0 16190 0 --:--:-- --:--:-- --:--:-- 16380
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 218k 100 218k 0 0 2098k 0 --:--:-- --:--:-- --:--:-- 2118k
[Fri May 31 13:17:57 UTC 2024] Installing from online archive.
[Fri May 31 13:17:57 UTC 2024] Downloading https://github.com/acmesh-official/acme.sh/archive/master.tar.gz
[Fri May 31 13:17:57 UTC 2024] Extracting master.tar.gz
[Fri May 31 13:17:58 UTC 2024] Installing to /root/.acme.sh
[Fri May 31 13:17:58 UTC 2024] Installed to /root/.acme.sh/acme.sh
[Fri May 31 13:17:58 UTC 2024] Installing alias to '/root/.bashrc'
[Fri May 31 13:17:58 UTC 2024] OK, Close and reopen your terminal to start using acme.sh
[Fri May 31 13:17:58 UTC 2024] Installing alias to '/root/.cshrc'
[Fri May 31 13:17:58 UTC 2024] Installing alias to '/root/.tcshrc'
[Fri May 31 13:17:58 UTC 2024] Installing cron job
[Fri May 31 13:17:58 UTC 2024] Good, bash is found, so change the shebang to use bash as preferred.
[Fri May 31 13:17:58 UTC 2024] OK
[Fri May 31 13:17:58 UTC 2024] Install success!
[Fri May 31 13:17:58 UTC 2024] Removing cron job
[Fri May 31 13:17:58 UTC 2024] LE_WORKING_DIR='/root/.acme.sh'
[Fri May 31 13:17:58 UTC 2024] Changed default CA to: https://acme-v02.api.letsencrypt.org/directory
[Fri May 31 13:17:59 UTC 2024] Uninstalling alias from: '/root/.bashrc'
[Fri May 31 13:17:59 UTC 2024] Uninstalling alias from: '/root/.cshrc'
[Fri May 31 13:17:59 UTC 2024] Uninstalling alias from: '/root/.cshrc'
```Step Three: Make sure the domain you're using points to your Loadbalancer appliance
- Before running through the process of issuing a certificate, make sure the domain of your choice points to your Loadbalancer:
; <<>> DiG 9.18.27 <<>> le.loadbalancer.ing
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 60338
;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 1232
;; QUESTION SECTION:
;le.loadbalancer.ing. IN A
;; ANSWER SECTION:
le.loadbalancer.ing. 15 IN A 20.117.188.145
```- Now, from your Loadbalancer.org appliance, run the below command to issue the certificate.
lb-letsencrypt.sh -i -p 443 -h 8888 -d le.loadbalancer.ing
-i for issue
-p 443 specifying that our website listens on port 443
-h 8888 specifying the port on which the acme.sh responds
-d followed by the domain for which you wish to issue a certificate
- Then just wait until you see the below appearing in your terminal:
Successfully issued and uploaded new cert le.loadbalancer.ing, finished.
The full output of steps two and three will therefore look like this:
Process Stunnel is running, continuing.
We do not have a Secondary node
WUI Username:
loadbalancer
WUI Password:
[Fri May 31 13:18:08 UTC 2024] Using CA: https://acme-v02.api.letsencrypt.org/directory
[Fri May 31 13:18:08 UTC 2024] Standalone mode.
[Fri May 31 13:18:08 UTC 2024] Creating domain key
[Fri May 31 13:18:10 UTC 2024] The domain key is here: /root/.acme.sh/le.loadbalancer.ing/le.loadbalancer.ing.key
[Fri May 31 13:18:10 UTC 2024] Single domain='le.loadbalancer.ing'
[Fri May 31 13:18:12 UTC 2024] Getting webroot for domain='le.loadbalancer.ing'
[Fri May 31 13:18:12 UTC 2024] Verifying: le.loadbalancer.ing
[Fri May 31 13:18:12 UTC 2024] Standalone mode server
[Fri May 31 13:18:14 UTC 2024] Pending, The CA is processing your order, please just wait. (1/30)
[Fri May 31 13:18:17 UTC 2024] Success
[Fri May 31 13:18:17 UTC 2024] Verify finished, start to sign.
[Fri May 31 13:18:17 UTC 2024] Lets finalize the order.
[Fri May 31 13:18:17 UTC 2024] Le_OrderFinalize='https://acme-v02.api.letsencrypt.org/acme/finalize/1756328112/274219995702'
[Fri May 31 13:18:18 UTC 2024] Downloading cert.
[Fri May 31 13:18:18 UTC 2024] Le_LinkCert='https://acme-v02.api.letsencrypt.org/acme/cert/046fa506c6619bdff64033067fffcc5d7c72'
[Fri May 31 13:18:19 UTC 2024] Cert success.
-----BEGIN CERTIFICATE-----
MIIF9TCCBN2gAwIBAgISBG+lBsZhm9/2QDMGf//MXXxyMA0GCSqGSIb3DQEBCwUA
MDIxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MQswCQYDVQQD
EwJSMzAeFw0yNDA1MzExMjE4MThaFw0yNDA4MjkxMjE4MTdaMB4xHDAaBgNVBAMT
E2xlLmxvYWRiYWxhbmNlci5pbmcwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIK
AoICAQDI2B9Q04fd1mdjtQBotiqcinB5+PI4iRuOyR2/AXOVb/pr3jCxBEmJS4Y6
bZ0AntLUZHiMLZUXyHAOHJghun0XtJ0OvJf9AgmsCZ0mQRZvYe0yEemxMHJ0+gql
DrfCBeOX1tHQg9p+7X62s/beg6PYrPgNw215Zfl/WjZmt7c3NMNZj8SMbOF65txw
stIAnf6tKwzaWWhP33TOhh1mRVPlFTWDW6q2e8HD3jccQi2tGUGUUZUgQ4U7zdtZ
cIknteFaFvN5MluflvPZwW04UsdL2a3R0/f9Xj4TkHbUzRJ9rq46cYU0CyHVTYXH
IWurOVzBgM9HOLFv6yDAc7cyL0eLgxU2azZTGBm7EClyyJ+bE5b0To5jqNNQ0S0v
n8qd66KgXlGx4/dwpYZof8p7rR3rdsHCsitT/FRl20j1cCAfeW0nP8dvyNebxOj1
FMXqZncMgmDaqQpOMVJww28yBg/E78NXB6JNay+WOrcAIlkBuUlcDWABMPbPnXld
nJ+lmgFHYtaZ8KVpwIDe+9Sg3DSztcXlH0t2KTMPTwCmk6TpLZ6bMAFSa17M0pg6
vsZxpH4GFIn9U4As8aUpdW9QJQQQe6P6Cf9ugZX01hcprNIcnV3hbTl8fj6oeZLr
pXPQCJrtX5rit/7nBE1sxHHMuBZDP39okNAE97D4E3Ngtbbr+wIDAQABo4ICFzCC
AhMwDgYDVR0PAQH/BAQDAgWgMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcD
AjAMBgNVHRMBAf8EAjAAMB0GA1UdDgQWBBQ7JI/Rogg/Si37j/OctVPCUAx09zAf
BgNVHSMEGDAWgBQULrMXt1hWy65QCUDmH6+dixTCxjBVBggrBgEFBQcBAQRJMEcw
IQYIKwYBBQUHMAGGFWh0dHA6Ly9yMy5vLmxlbmNyLm9yZzAiBggrBgEFBQcwAoYW
aHR0cDovL3IzLmkubGVuY3Iub3JnLzAeBgNVHREEFzAVghNsZS5sb2FkYmFsYW5j
ZXIuaW5nMBMGA1UdIAQMMAowCAYGZ4EMAQIBMIIBBgYKKwYBBAHWeQIEAgSB9wSB
9ADyAHcAdv+IPwq2+5VRwmHM9Ye6NLSkzbsp3GhCCp/mZ0xaOnQAAAGPzs0X5gAA
BAMASDBGAiEAz+d9mFW4CIftZNyRWR/NWG3rfFfwC1ktr5mO4rLE8bQCIQDFe5fQ
y3qyIMy0VETkdZXDRCZLZUs1NrOjreLCsfucAAB3AN/hVuuqBa+1nA+GcY2owDJO
rlbZbqf1pWoB0cE7vlJcAAABj87NGHgAAAQDAEgwRgIhAP6hnnJqboGlHyCnpp3V
tIgMyB+CP9pd+UTSmP5OxHl9AiEA78du+N/R2Dwor1xdNQWIxO5T9WQmORmgDZXK
gexYxjcwDQYJKoZIhvcNAQELBQADggEBAB9upOvDcVYFQQ7cckxucjoZUeLaZjQj
XoCE/rMX9u3iUizH6U069BiizU9PwaA5HE2w4ahpD4OABTqdLCKfDxWU4pDAq/+p
k9khaXe9n0Ei3DAoSWpCmb9tF8wzlsLPwuZc3p5XNLeq3FWOvCYZ7qSowuyzAmJF
tgN29SrO8U+r1v2U0AEO30bOqyGWfLexk/ve0fAk8W4p/jqgMkGAUyMUhbsFedu+
LCqP+LLeomctxIomDXj9FASW8xDUA4ajNeTTCH8MP4mP6NY9uFHnRihwybwpv4wL
PwcMQ6+K435dPSvGFzAdWtUrwVTSv7c2Hj2JUwRlS9dmMcu6dR1EBh8=
-----END CERTIFICATE-----
[Fri May 31 13:18:19 UTC 2024] Your cert is in: /root/.acme.sh/le.loadbalancer.ing/le.loadbalancer.ing.cer
[Fri May 31 13:18:19 UTC 2024] Your cert key is in: /root/.acme.sh/le.loadbalancer.ing/le.loadbalancer.ing.key
[Fri May 31 13:18:19 UTC 2024] The intermediate CA cert is in: /root/.acme.sh/le.loadbalancer.ing/ca.cer
[Fri May 31 13:18:19 UTC 2024] And the full chain certs is there: /root/.acme.sh/le.loadbalancer.ing/fullchain.cer
Successfully issued and uploaded new cert le.loadbalancer.ing, finished.```Step Four: Apply the certificate to our SSL Termination
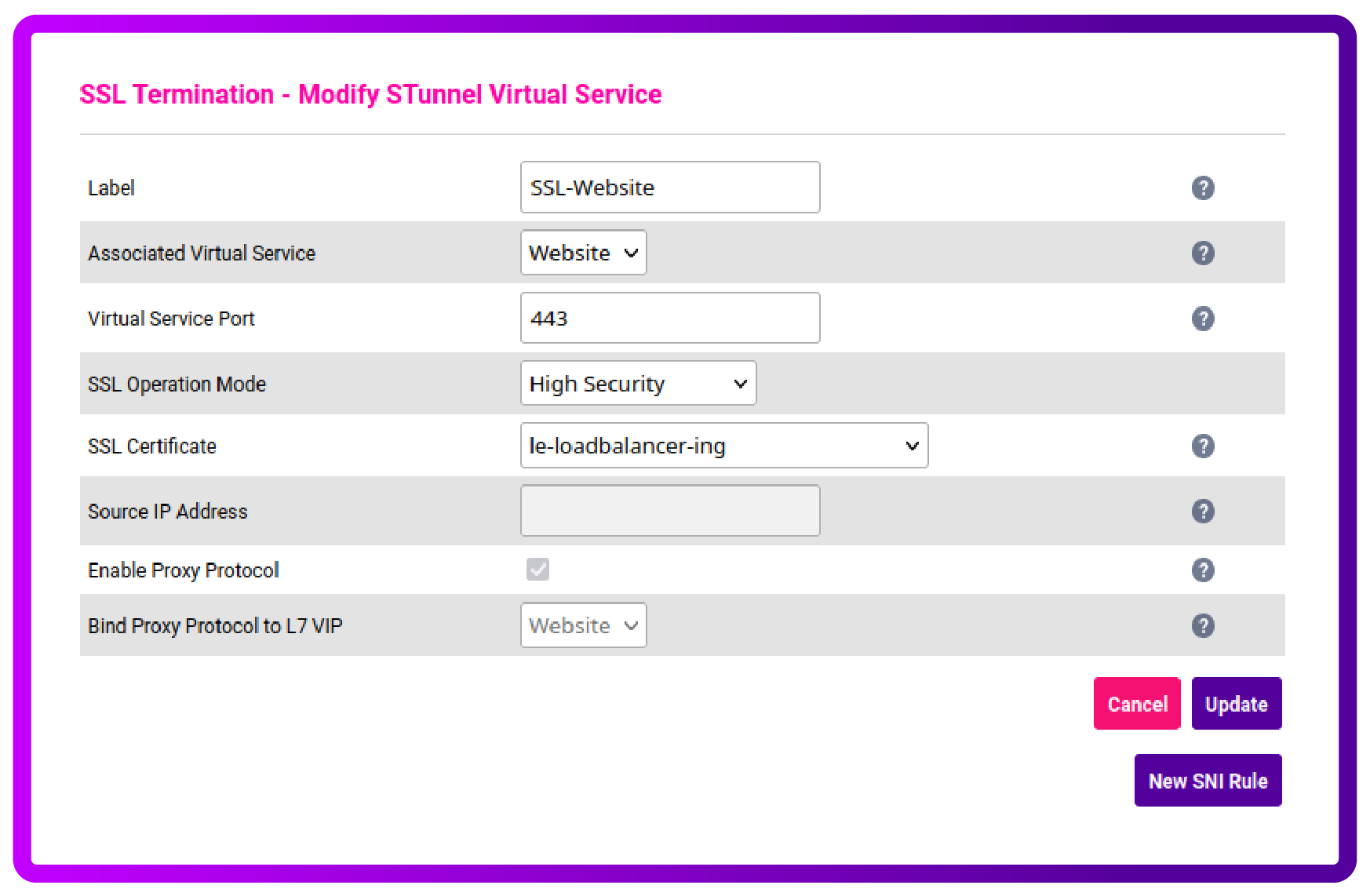
Now, let’s go back to the WebUI and apply the certificate to our Termination:
- Navigate to Cluster configuration and then SSL Termination.
- Click on Modify button by the name of your service.
- In the SSL Certificate dropdown menu, select the name of your newly issued certificate.
- Click Update to save the configuration.
- Reload Stunnel and HAProxy, and enjoy your free-of-charge TLS certificate!
Step Five: Setup CronJob for automation
CronJob creates Jobs on a repeating schedule and is perfect for what we're trying to do here, i.e. renewing the certificate automatically.
- Go back to your SSH session and run:
crontab -e
- To edit your crontab, type in a line similar to the below, and save the file:
`0 0 * * * lb-letsencrypt.sh -p 443 -d le.loadbalancer.ing > /dev/null`
Demo video: How to automate SSL/TLS certificate renewal with Let's Encrypt
For those of you who prefer video, here are the steps to follow:
Putting it all together
So, let's return to the question I posed at the beginning: "How many engineers does it take to renew an SSL/TLS certificate?" The answer should be none!!!
By following the steps above, you should have successfully configured your Loadbalancer.org appliance to automatically handle Let's Encrypt challenges and renew your TLS certificates seamlessly. Job done! So you can keep your connections secure, and find other things to do with all that free time you've managed to claw back. I'm sure you can think of just a few other jobs that need doing. Such is the life of a SysAdmin...
















