So you're probably here because you want to know how to achieve an A+ rating for your SSL web server on Qualys. A quick fun fact: did you know the A+ and A rating are in fact the same? The "+" just shows that you have gone the extra mile in the name of security; the difference is enabling HSTS (HTTP Strict Transport Security). In short, HSTS enforces the browser to always use HTTPS once a certain response header is presented. This is brilliant for mitigating various SSL stripping attacks and also prevents the constant need to 301 clients from HTTP to HTTPS. There is another way to achieve an A+ and that is by adding DNSSEC. You can either have HSTS, DNSSEC or both, but this would be done at the DNS level and not the load balancer.
Beware: Enabling HSTS before your website is ready to use HTTPS can cause a lot of issues. Be sure all proper certificates are in place before enabling.
More info can be found on the HSTS Wikipedia and the DNSSEC Wikipedia.
What ciphers will be needed to achieve an A+ rating?
Well, we have done some testing and we have found the following cipher suite gives an A+ rating. Out of interest, this is the same cipher suite we use by default in our product under the "High security" option.
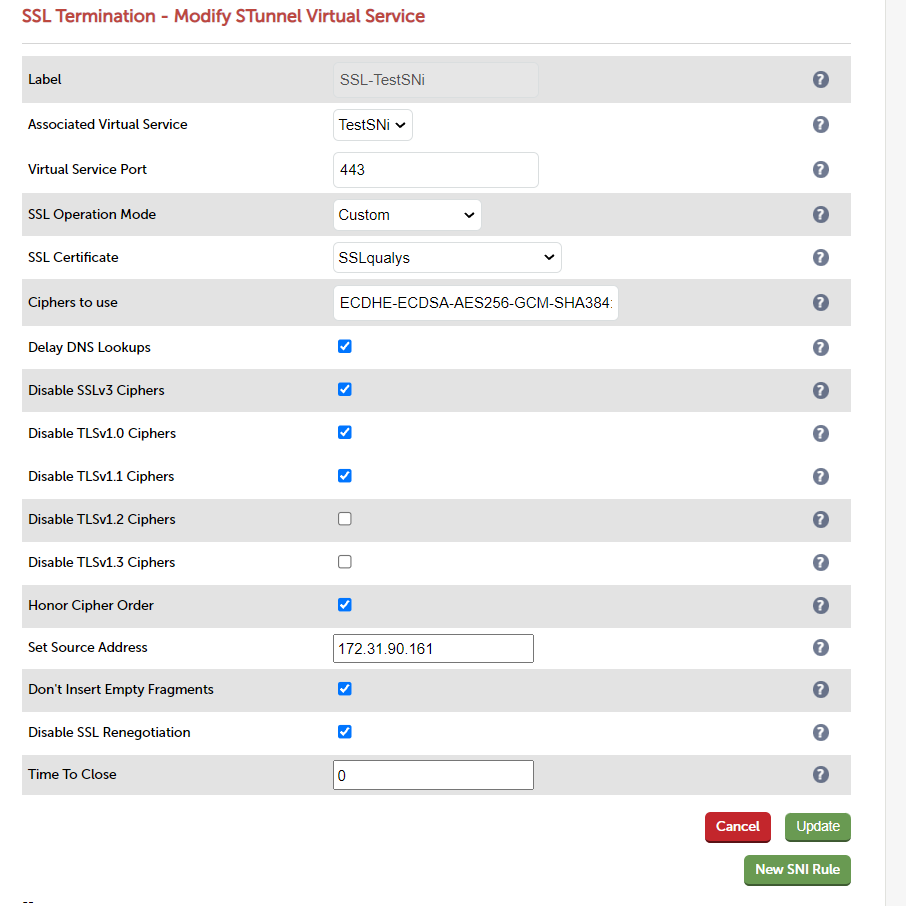
ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256
If you're creating a HAProxy manual configuration we have a full list of ciphers we use within the product and their different uses in our Loadbalancer.org manual.
HAProxy example configuration
Here is an example HAProxy configuration using the above ciphers:
global
ssl-default-bind-ciphers ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256
frontend TestSNi
bind 172.31.90.161:80 transparent
bind 172.31.90.161:443 ssl crt /etc/loadbalancer.org/certs/server.pem transparent
http-request redirect scheme https code 301 unless { ssl_fc }
http-response set-header Strict-Transport-Security "max-age=16000000; includeSubDomains; preload;"
mode http
...
You can see in the above example that as well as the ciphers, I have added a http-response:
http-response set-header Strict-Transport-Security "max-age=16000000;
This will cause HAProxy to return the strict-transport-security header (the header I previously mentioned that will instruct browsers to route to HTTPS from the start). I have added the "max-age" of 16000000 so the rule lasts for the next 6 months after a user has visited your website. Another positive but lesser known side effect is that the header will cause traffic to avoid round trips between the user and the server, causing a decrease in response times.
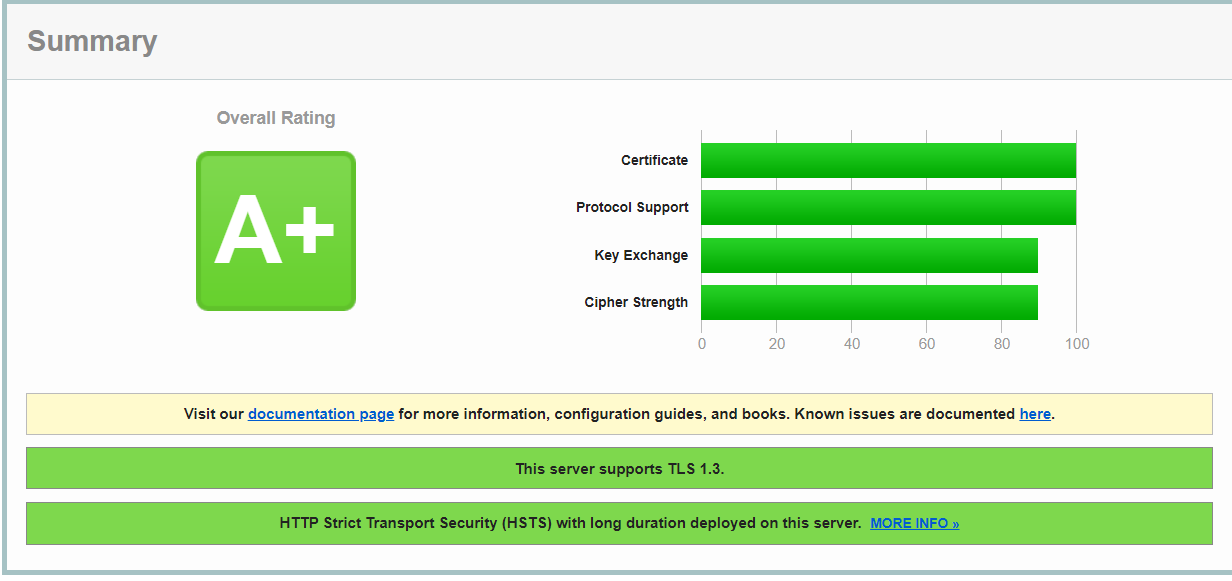
Once the header has been added, it returns an A+ Qualys rating.
Note: At the bottom of the screenshot, you can see HSTS has been enabled
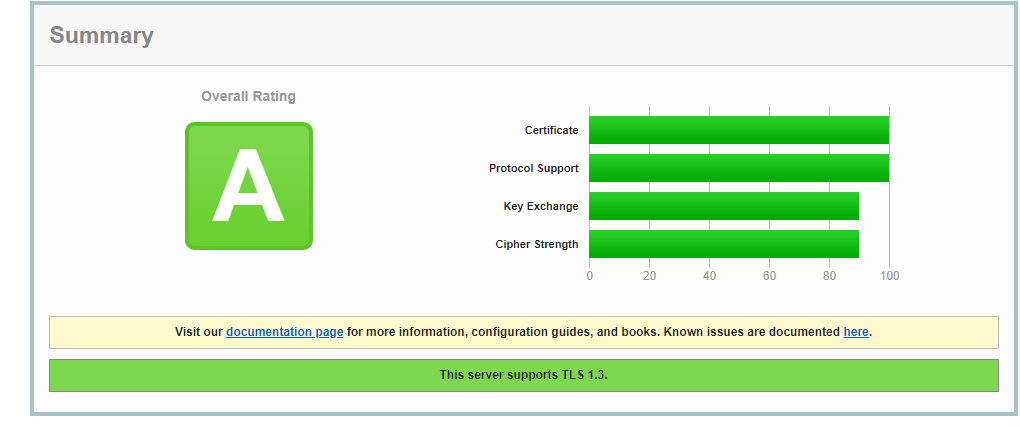
Without HSTS the test returns just the A. Confirming HSTS is needed to get the A+ as this was tested with the same certificate and ciphers.
How to achieve A+ on the Loadbalancer.org appliance
So, I have gone through how to get an A+ using HAProxy, but how do we do this on our appliance? Well, it's actually really straight forward. We have an extremely detailed blog on that here, but to save you reading the whole thing I will summarise it briefly below.
Our appliance supports SSL terminations so you can terminate with a self signed certificate, or you can upload a prepared PEM or PFX file to use. You can also generate a CSR to send to a certificate authority to get signed. We also natively support letsencrypt on our appliance. To generate a letsencrypt certificate, follow this awesome blog written by my colleague Rob Congalton.
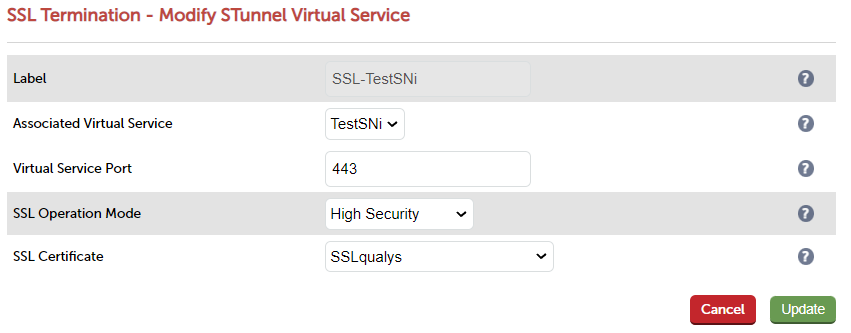
Once you have your certificate, attach it to your SSL termination and then choose the virtual service you want to terminate to. We have a range of default SSL operation modes, such as "High Security" "FIPs Compliant" and "high compatibility". These options can be found under the WebUI -> "Cluster Configuration" -> "SSL Termination".
The option of "custom" allows you to choose which Ciphers you wish to enable or disable.
"But I just want the damn A, how do I achieve it?" I hear you cry! Well, all you need to know, is by using our "High security" with a signed certificate, this will get you the glorified A. If you use a self signed certificate, you will get the lowest score of a "T" because the certificate has not been signed.
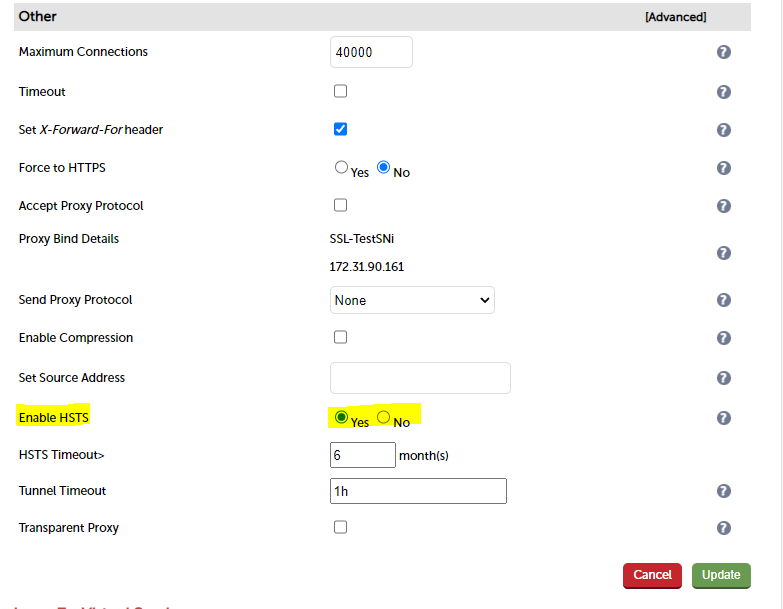
"What about the plus?" Well, the plus can be gained from a simple tick box when modifying the virtual service. If you modify your virtual service and scroll all the way to the bottom and select "Advanced" on the "Other" header, it reveals the all important "Enable HSTS" option!
TA DA!
So, if you have got a signed certificate, and enabled HSTS on our load balancer, you should now be achieving an A+ Qualys rating. If you have further questions about SSL terminating on your Loadbalancer.org appliance please get in touch and we will be happy to help!
Beware: Enabling HSTS before your website is ready to use HTTPS can cause a lot of issues. Be sure ALL proper certificates are in place before enabling.