
This blog explains how to assess and identify F5 BIG-IP* vulnerabilities using different diagnostic tools, and how to remediate the detected vulnerability.
It also concludes with a set of recommendations to help you protect your environment, and specifically F5 systems, against CVE exploitation attacks!
How to assess F5 BIG-IP vulnerabilities
Eek, you've become aware of an F5 BIG-IP vulnerability. What next?! Well, your next steps depend on the following...
What category does your vulnerability fall into?
F5 investigates and prioritizes vulnerability reports based on the potential exploitability of the system and communicates the vulnerability impact using Common Vulnerability Scoring System version 3 (CVSSv3).
F5 uses the full breadth of CVSSv3 and provides scores based on available information that F5 deems appropriate:
| CVSS score | Severity of vulnerability |
|---|---|
| 9.0-10.0 | Critical |
| 7.0-8.9 | High |
| 4.0-6.9 | Medium |
| Below 3.9 | Low |
F5 assigns Common Vulnerability and Exposures (CVEs) and publishes security advisories for all vulnerability categories, from Low to Critical.
F5 also publishes security advisories for security exposures, which do not affect the confidentiality, integrity, and availability (CIA) of the F5 product, but may impact the CIA of one of the following:
- Services or network traffic processed by the F5 product
- Confidentiality of data cached on the F5 product
Security exposures are generally dependent on configuration and use of the F5 device. Therefore, F5 cannot produce an accurate CVSS score or severity for security exposures.
F5 recommends customers treat security exposures as a high priority and evaluate the specific severity of these issues in their own environment.
How to identify F5 BIG-IP vulnerabilities
The identification of vulnerabilities can be done in several ways. Here are the methods proposed and supported by F5, and the steps needed to conduct them:
- The QKView file & iHealth diagnostic tool
- F5 Quarterly Security Notifications
- And the CVEdetails website
Its also a good idea to read this F5 document to help you understand how they describe the software version numbering system and how it correlates to CVEs.
Use the QKView file & iHealth diagnostic tool
1. Generate a QKView file on your BIG-IP system
The QKView utility is an executable program that generates machine-readable XML diagnostic data and combines the data into a single compressed Tape ARchive (TAR) file called a QKView. You can upload the QKView to the iHealth system, which translates the output and displays the content in a format similar to that of the Configuration utility.
Running the QKView utility from the Configuration utility (BIG-IP)
To run the qkview utility from the BIG-IP Configuration utility, perform the following procedure:
- Log in to the Configuration utility
- Go to System > Support
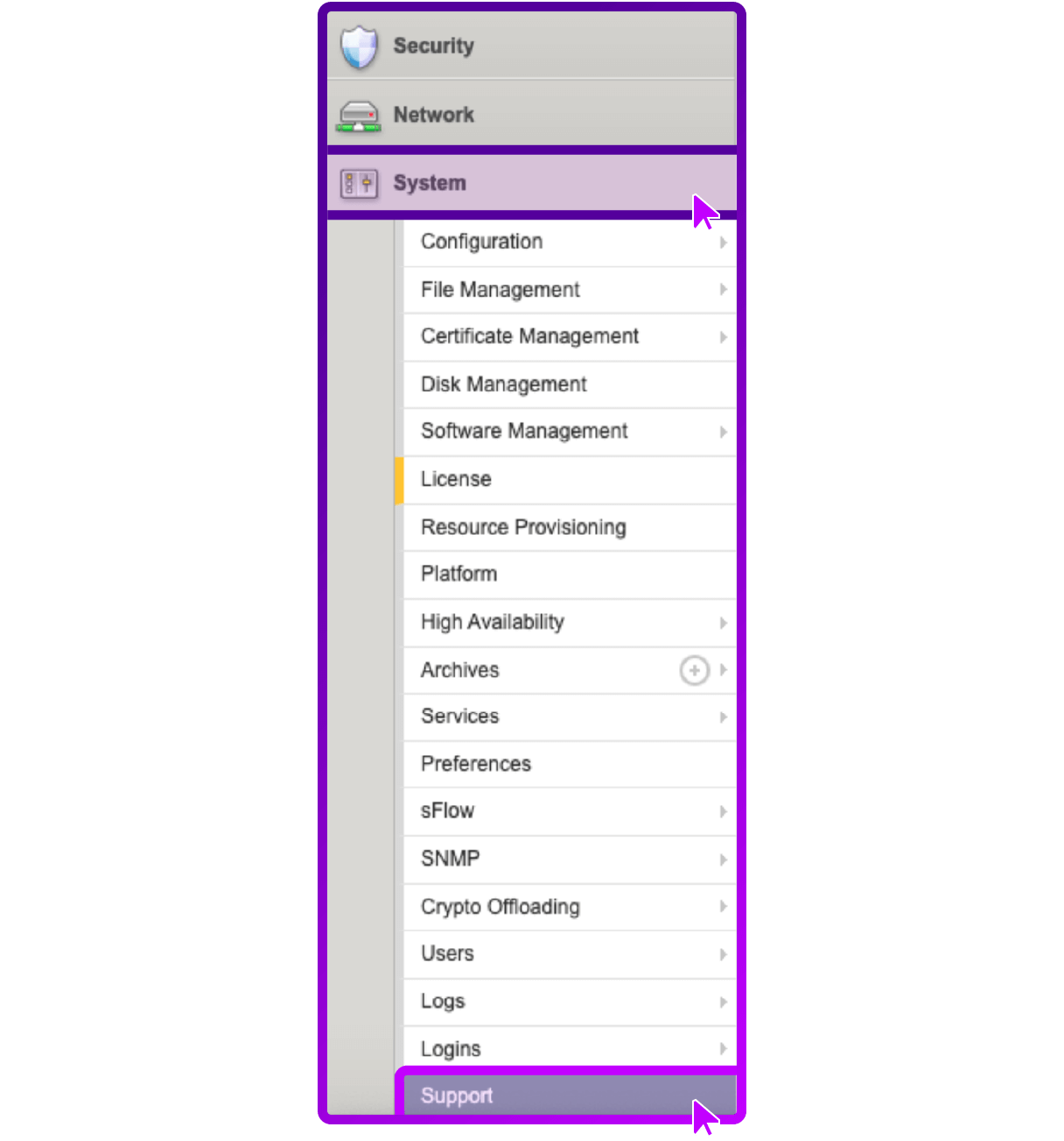
- Select New Support Snapshot
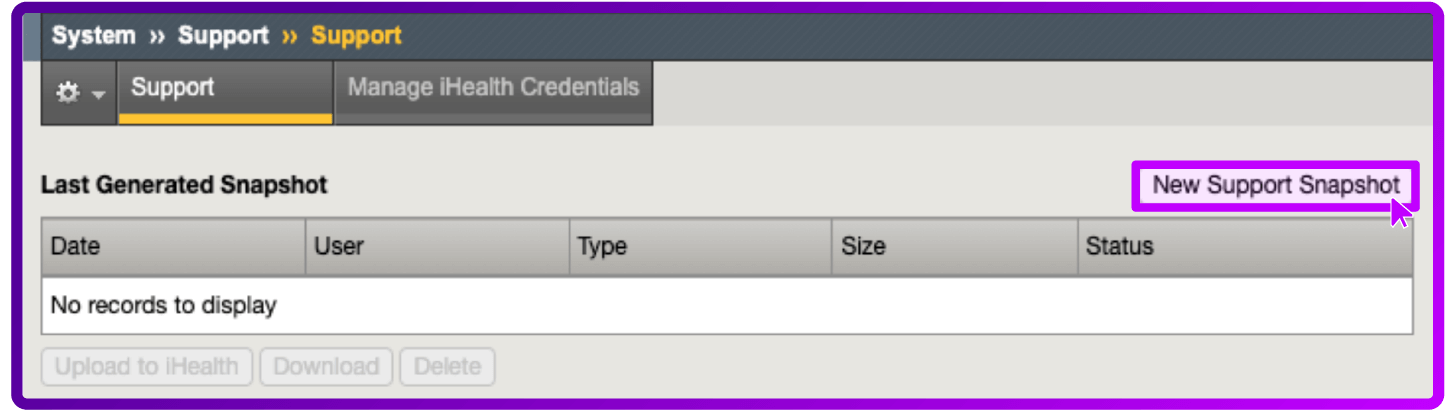
- For Health Utility, select Generate QKView
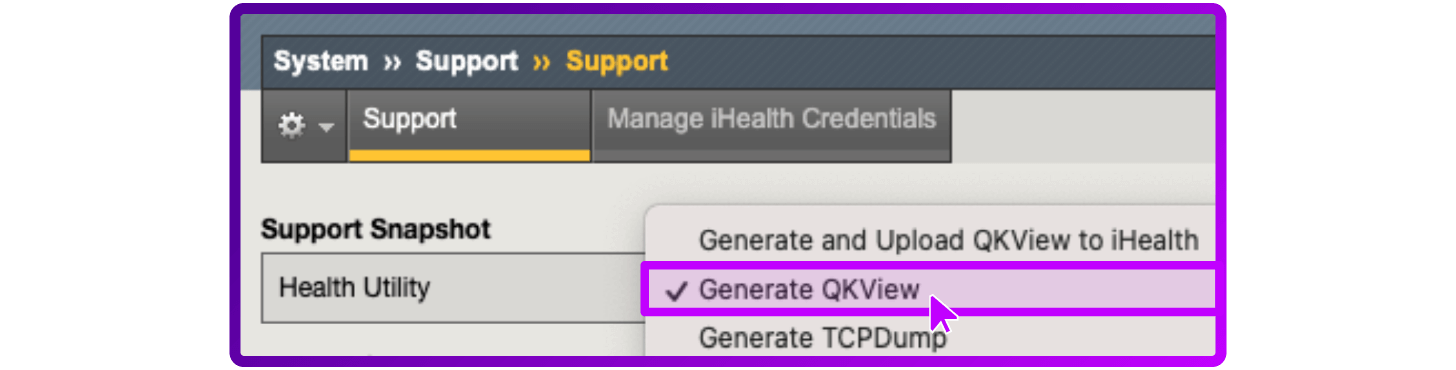
- Select Start
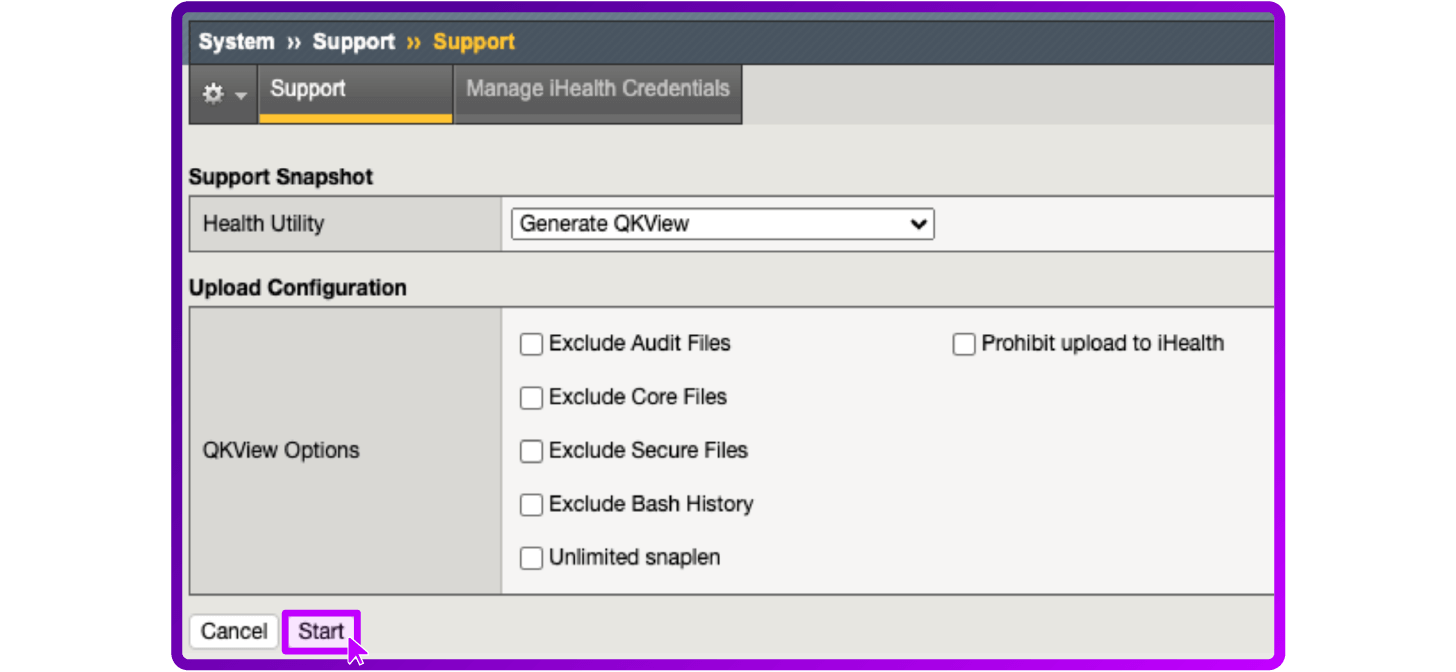
- Generating a QKView file in progress
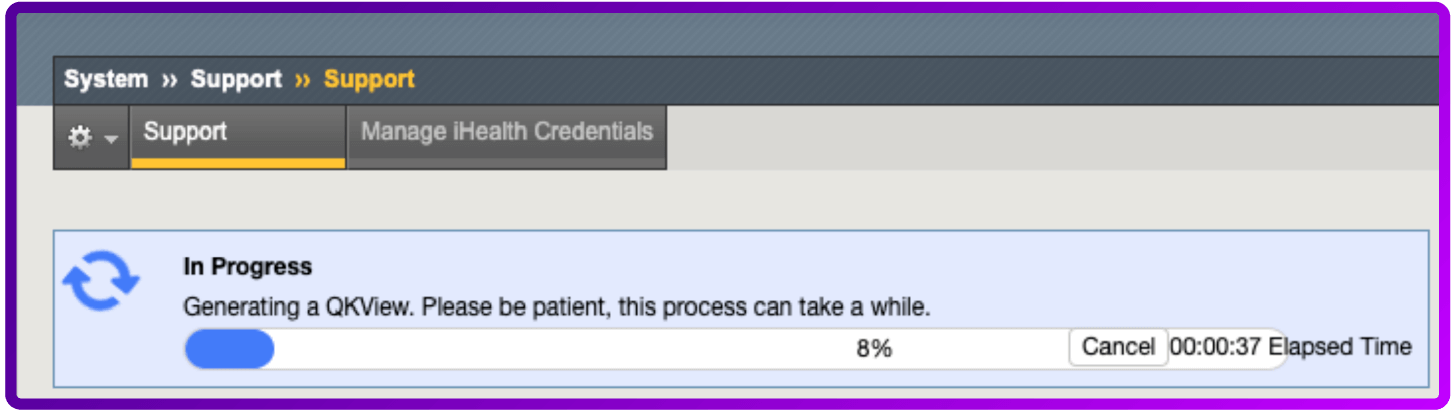
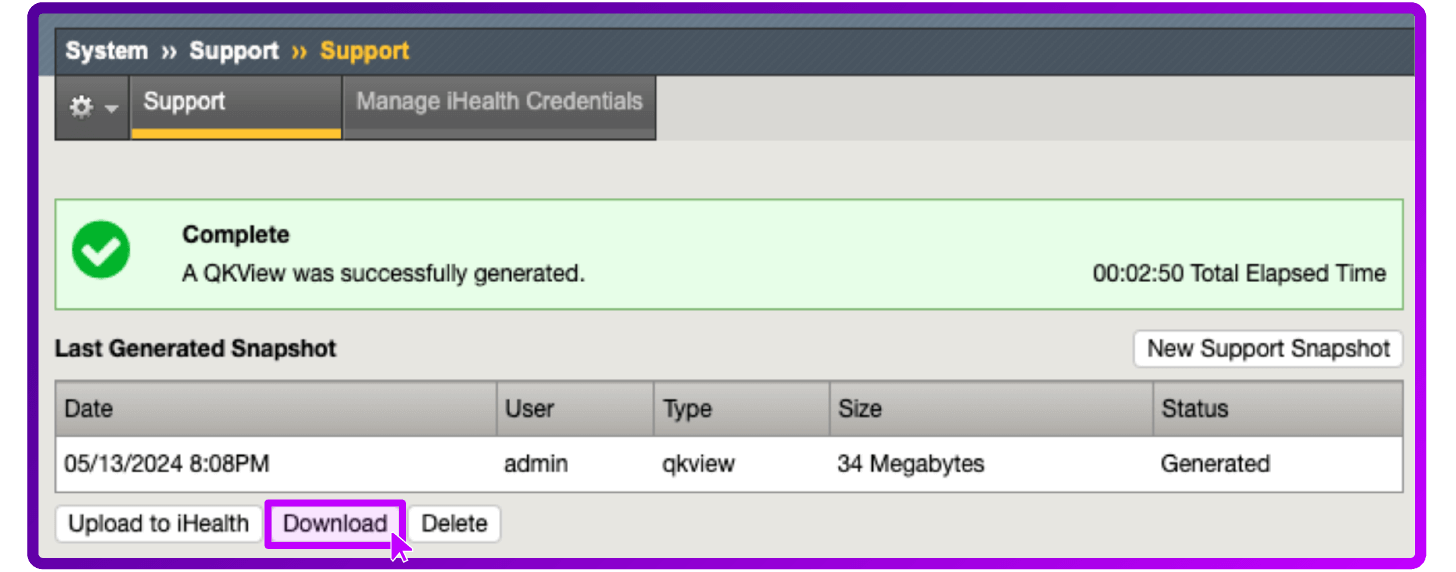
- To download the output file, select Download
Running the QKView utility from the command line (BIG-IP)
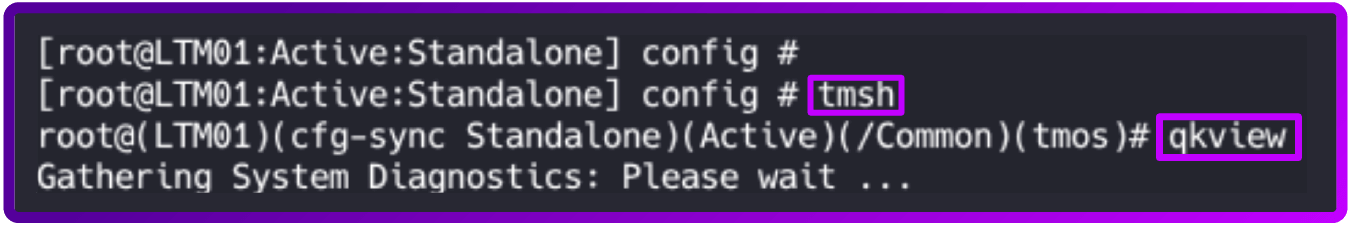
- Log in to the command line
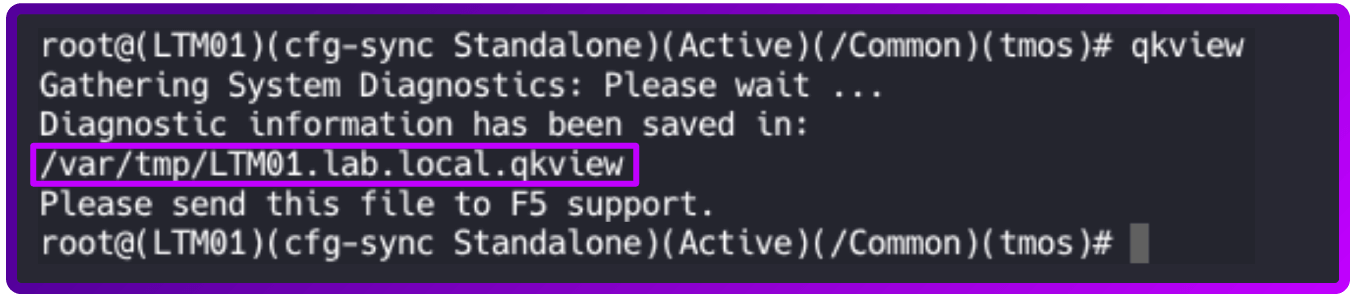
- To run the qkview utility, change to tmsh and enter the qkview command:
The output file name displays after the command has completed.
- Collect the output file from the /var/tmp/ directory by copying the file to an external host using a utility such as ftp or scp.
2. Uploading a QKView file to F5 iHealth
After you obtain the QKView diagnostic file, you can upload this file to F5 iHealth to diagnose the health and proper operation of your BIG-IP system.
To do that, perform the following procedure:
- Open a web browser and log in to the F5 iHealth site
- Note: BIG-IP iHealth is free but requires registration.
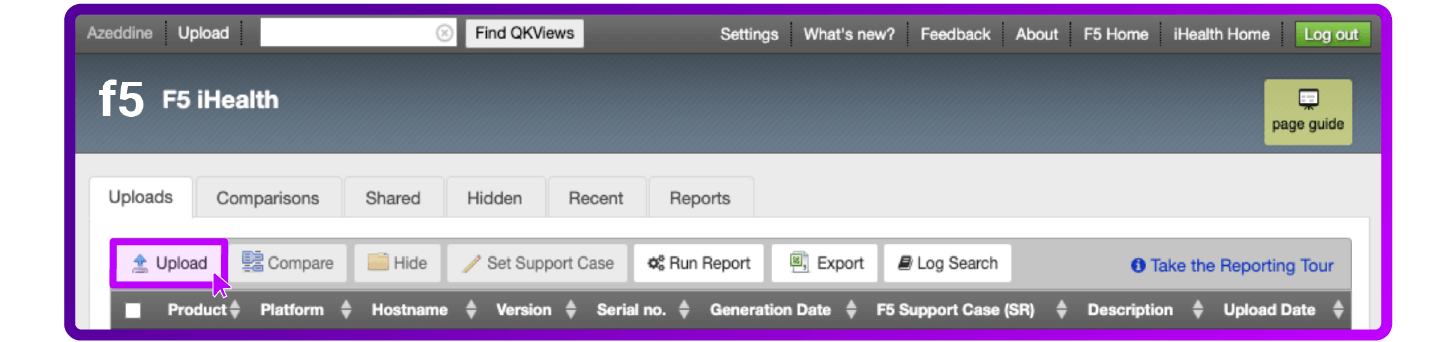
- Select Upload
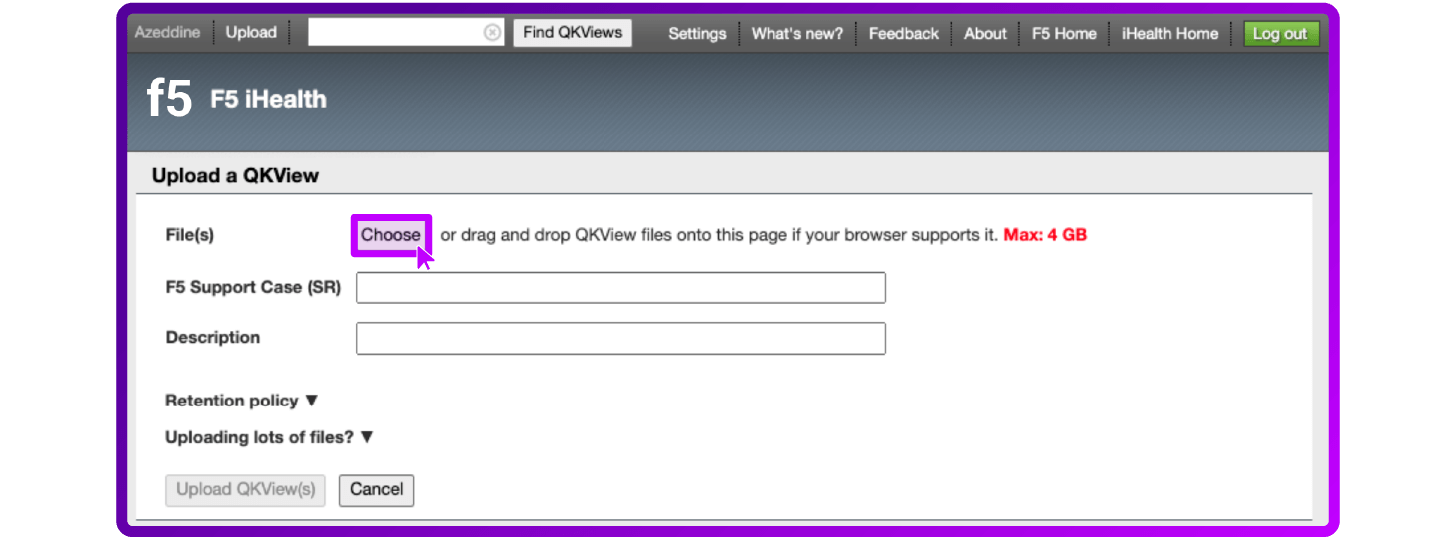
- Select Choose to select the Qkview file and click Upload QKview
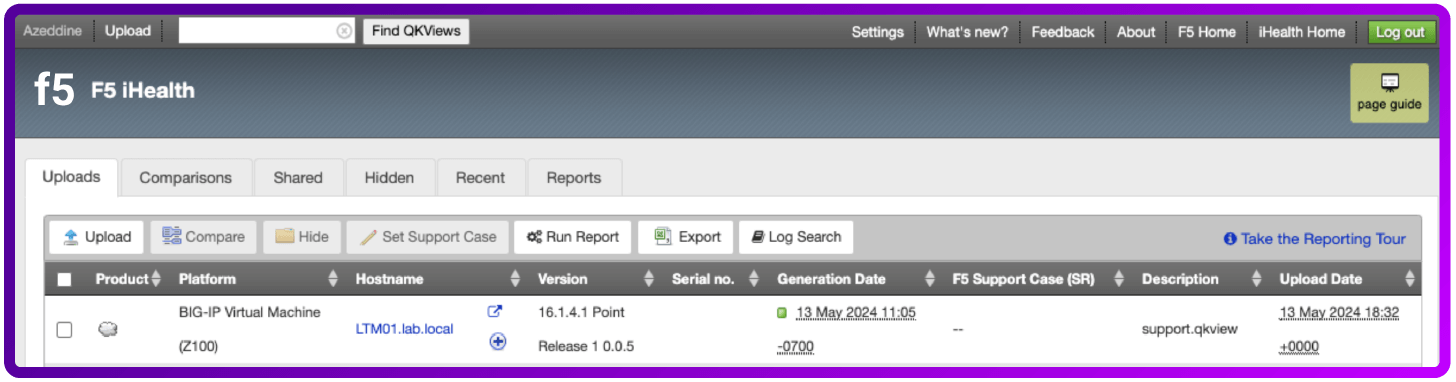
- Go to the QKView file on your local system
3. Using the BIG-IP iHealth diagnostic tool
iHealth Diagnostics evaluates the logs, command output, and configuration of your BIG-IP system against a database of F5 security vulnerabilities and exposures, some third-party vulnerabilities, known issues, common mistakes, and published F5 best practices. After you log in to iHealth you can review vulnerabilities to which your device may be susceptible.
- Log in to iHealth using your credentials
- Open the QKView file you uploaded by selecting the Hostname of your device
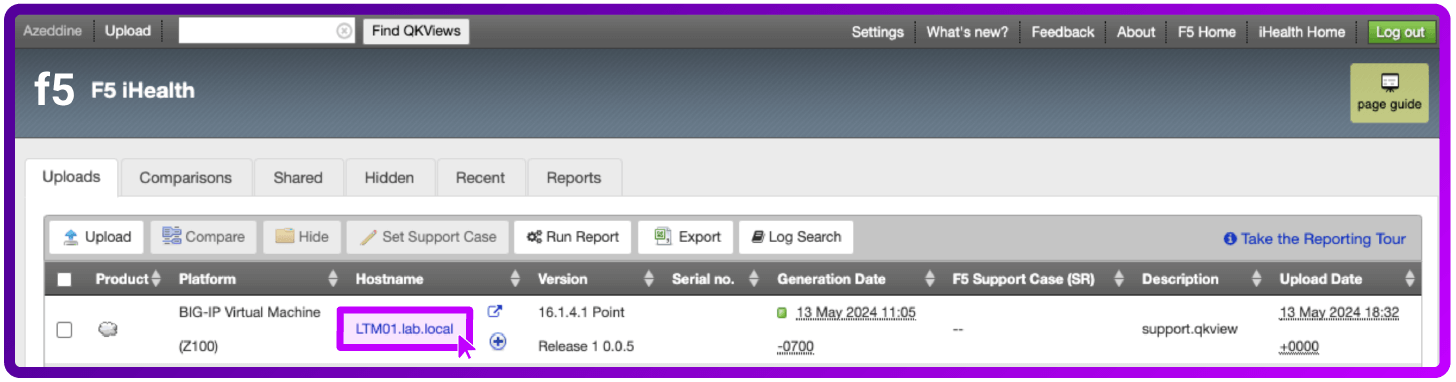
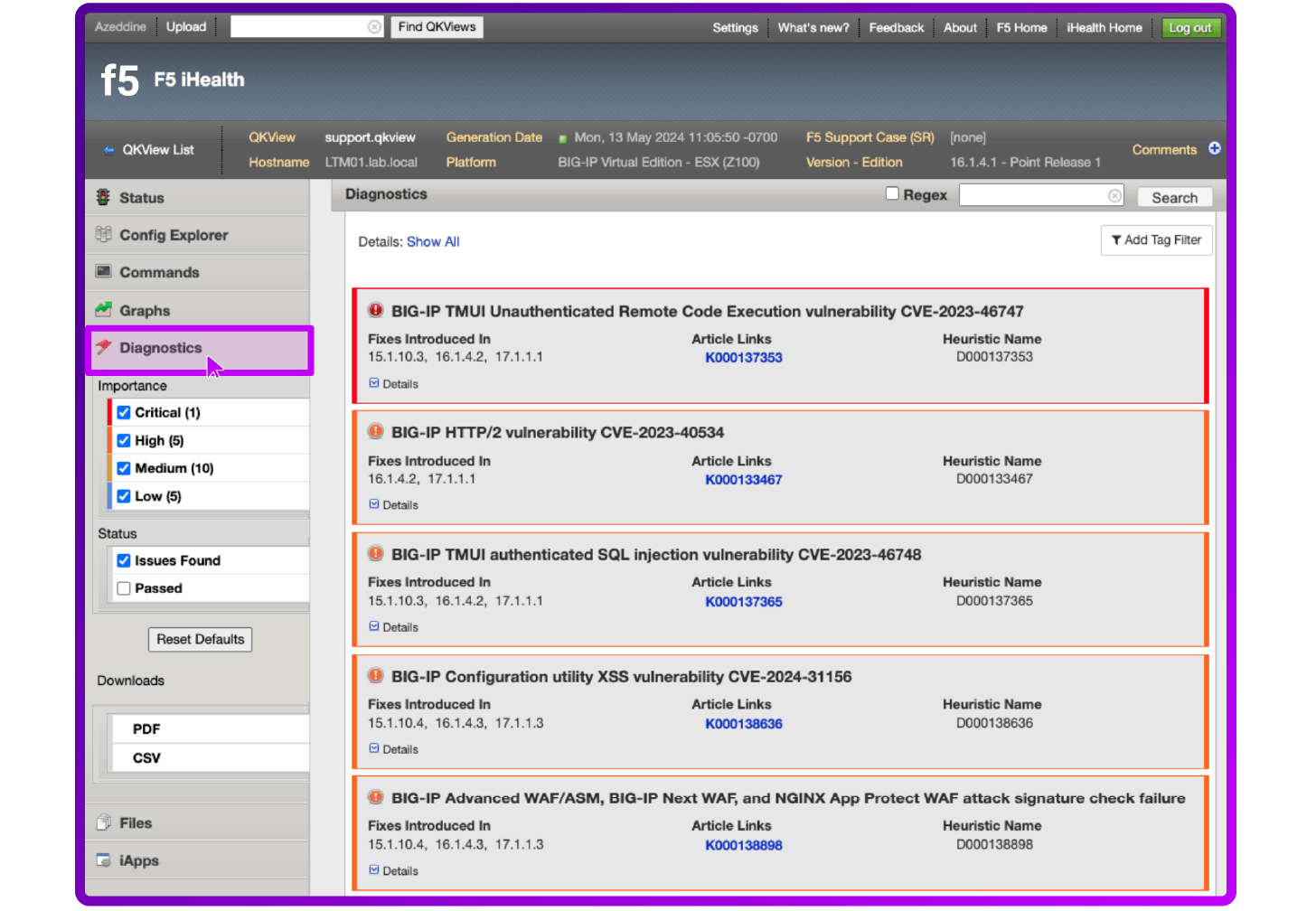
- Go to Diagnostics
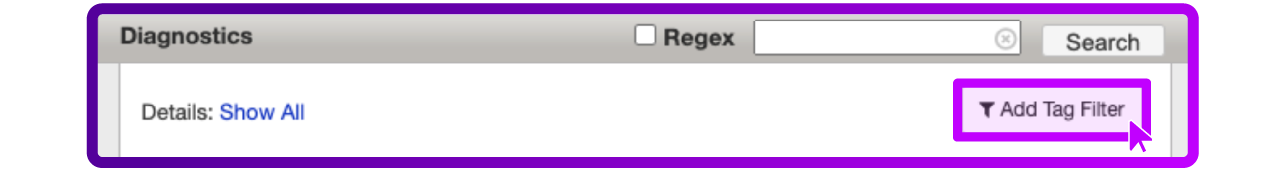
- Go to Add Tag Filter
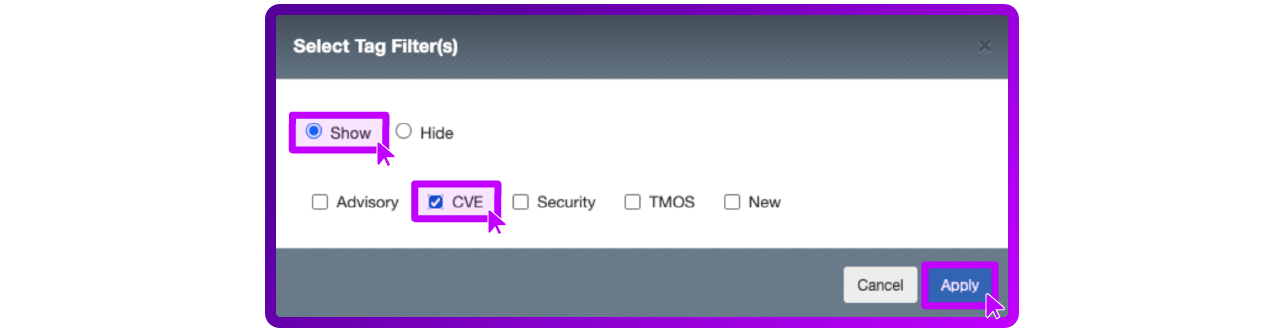
- Select Show and CVE as Filters
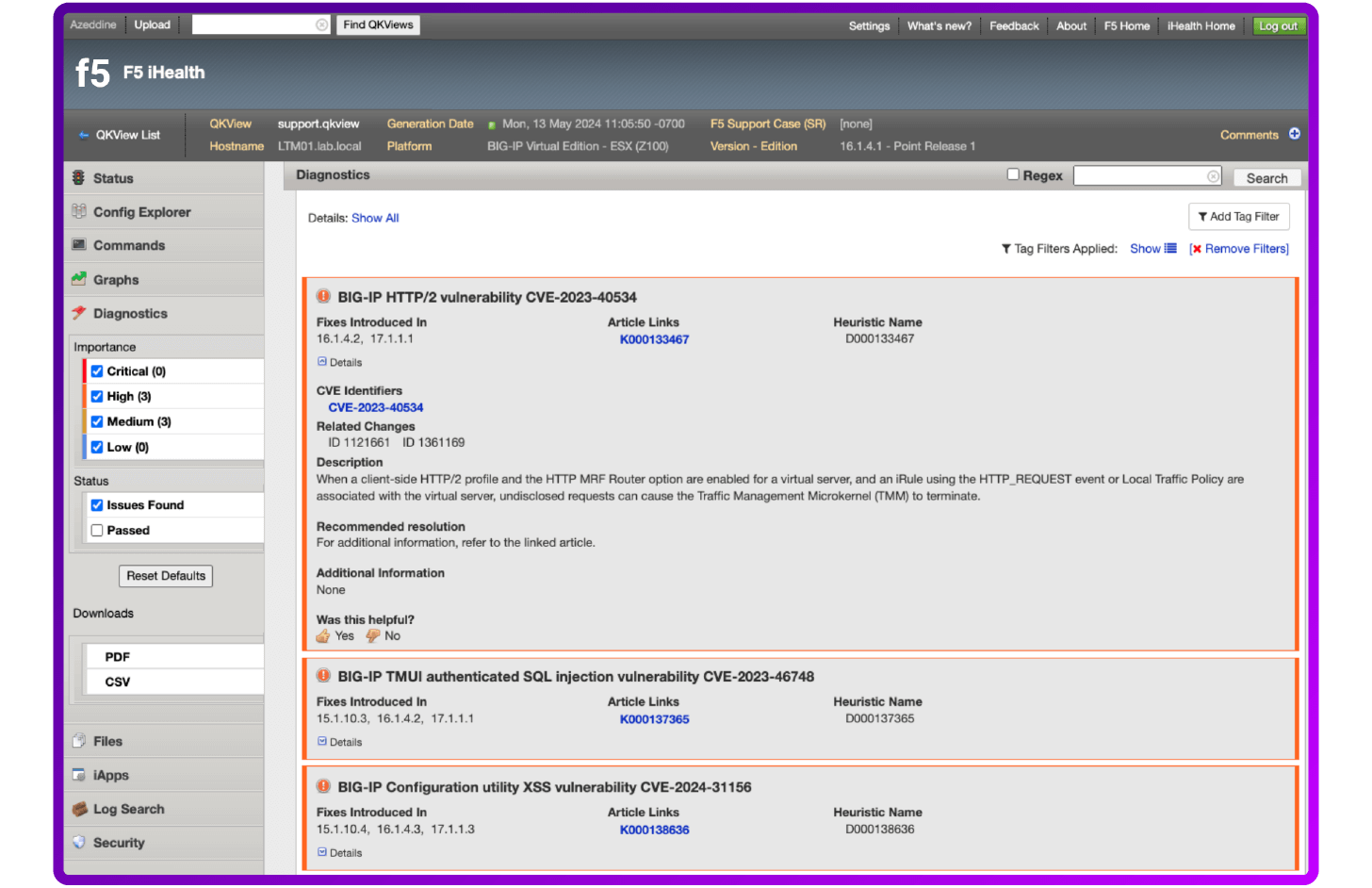
Then review all identified vulnerabilities or potential issues for this specific configuration object.
Review Quarterly Security Notifications
F5 discloses security vulnerabilities and security exposures for F5 products in Quarterly Security Notifications.
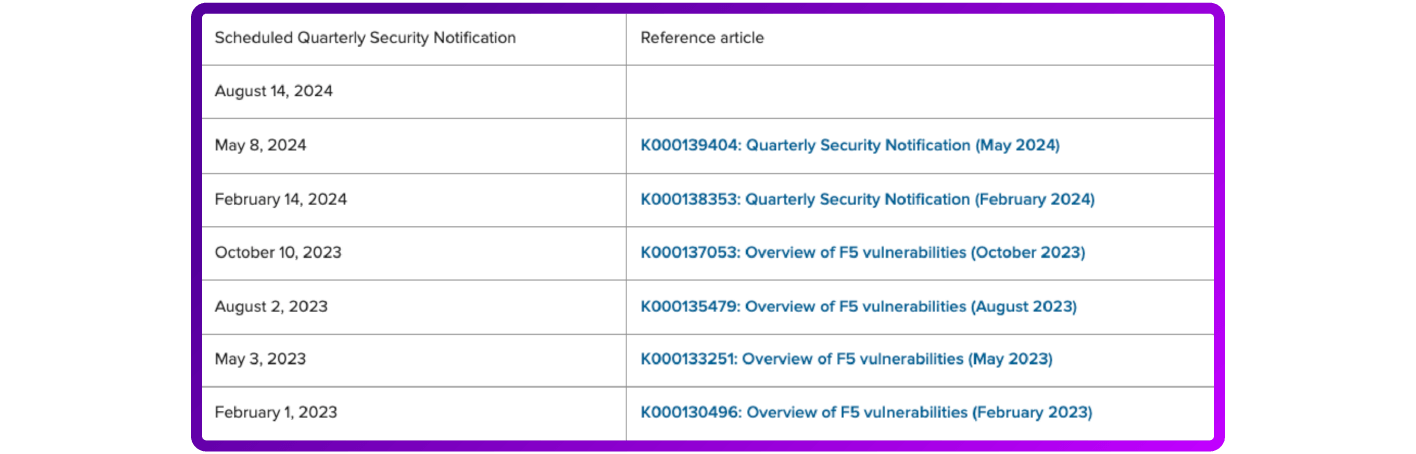
Quarterly Security Notification dates are published in advance so customers can schedule necessary updates in advance of the public disclosure date.
When it is necessary to disclose vulnerabilities at any time other than the scheduled Quarterly Security Notification, F5 will notify customers through an F5 Security Announcement, which will include links to Security Advisory articles containing detailed descriptions and steps to address the issue.
To sign up for F5 Security Announcements, including Quarterly Security Notifications, refer to the F5 Customer Preference Center.
The current and scheduled notifications are published by F5 on My5.
Here's an example Scheduled Quarterly Security Notification...
Check out the CVEdetails website
CVE Details is also a valuable resource for security engineers. It's an online database that provides comprehensive information about Common Vulnerabilities and Exposures (CVEs) reported in various software products. CVEs are standardized identifiers for security vulnerabilities, allowing for easier information sharing across the cybersecurity community.
CVE Details offers a searchable interface where you can explore CVEs based on different criteria, such as vendor, product, or severity. For each CVE entry, you can find detailed information, including a description of the vulnerability, its severity level, the date it was published, and any available solutions or workarounds.
Security engineers often use CVE Details to stay informed about the latest vulnerabilities affecting the software they are responsible for securing. By regularly monitoring CVE Details, they can assess the risks posed by different vulnerabilities and take proactive measures to mitigate them, such as applying patches or implementing security controls.
How to use CVEdetails.com
You can use CVEDetails to check for vulnerabilities in several ways (by category, by severity, by new CVEs …) in our case, we can use Vendor or product to directly check the CVEs related to F5 BIG-IP Systems:
- Search by Product: You can search for vulnerabilities based on a specific software product. Enter the name of the product in the search bar, and CVE Details will provide a list of vulnerabilities associated with that product.
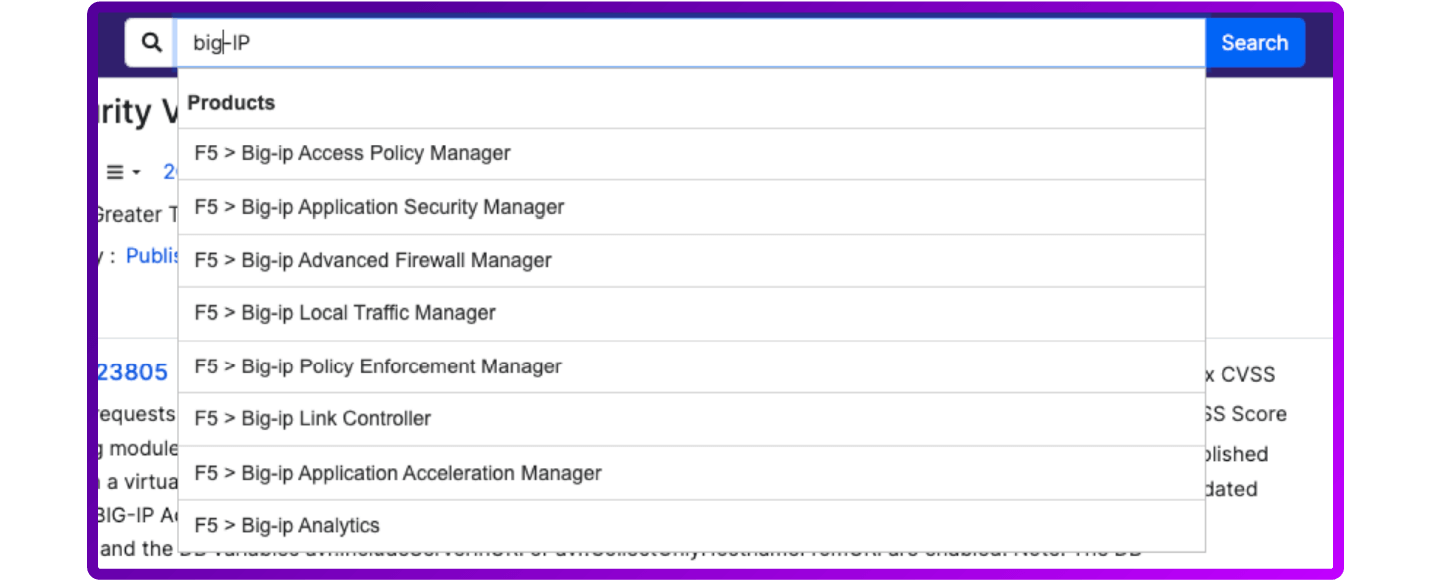
- Filter by Vendor: If you're interested in vulnerabilities related to a particular vendor's products, you can filter CVEs by vendor name. This allows you to see all vulnerabilities reported for products from a specific vendor.
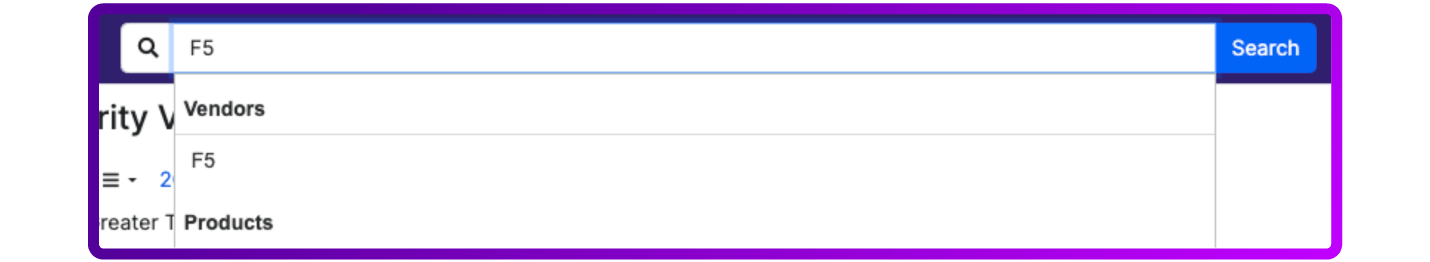
- Filter by version: You can also search for specific BIG-IP version
The result will look something like this:
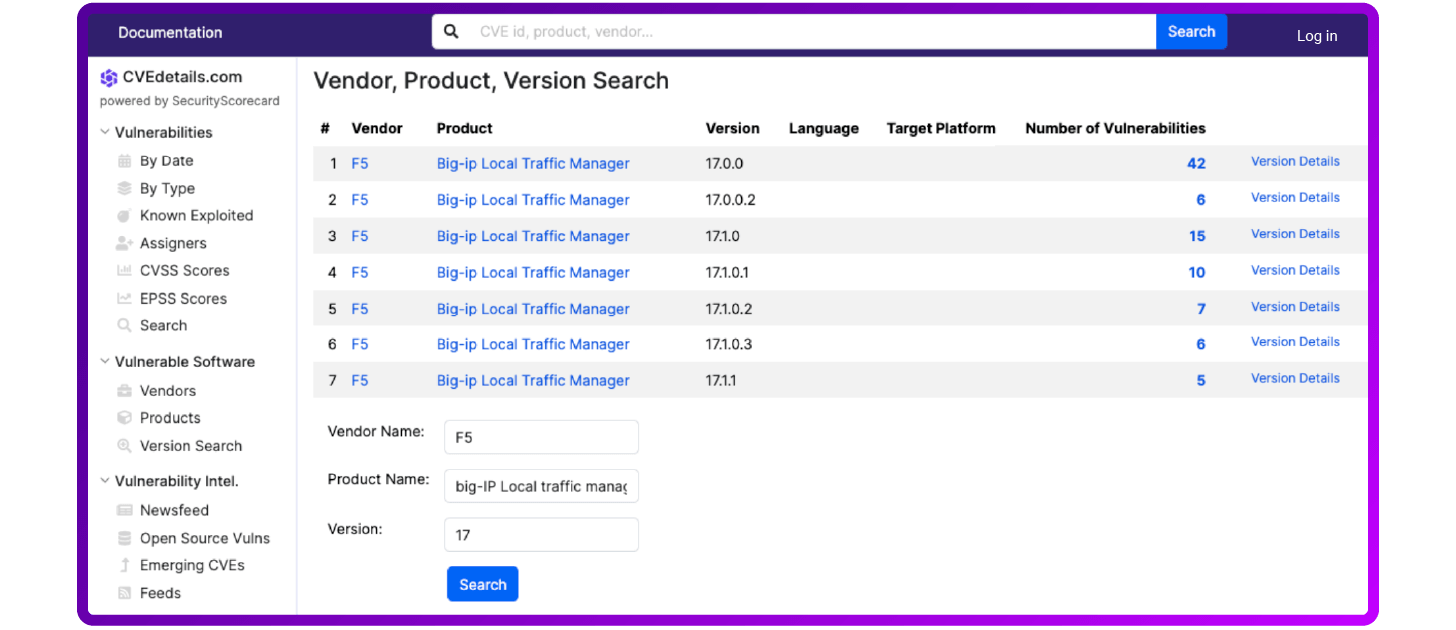
By using these features on CVE Details, you can effectively check for vulnerabilities and stay informed about potential security risks that may impact your organization's systems and infrastructure.
How to remediate F5 BIG-IP vulnerabilities
Each diagnostic result includes a summary of the identified issue, a suggested action to fix it, links to further information about the issue (such as AskF5 articles), and the heuristic name.
F5 recommends that you refer to the linked AskF5 article to determine if your device is known to be vulnerable, to see which components or features are affected by the vulnerability, and to find additional information about releases, hotfixes, or corrective actions to address the vulnerability.
Remediation of vulnerabilities can be done either by installing patches or by applying workaround and mitigation procedures.
1. Upgrade your F5 BIG-IP
Usually, an upgrade is the solution recommended by F5. Check out this step-by-step guide on how to upgrade F5 BIP-IPs.
2. Mitigation
The mitigation is the solution to apply if the patch is not immediately available, and involves implementing recommended workarounds provided by F5.
These may include configuration changes, disabling vulnerable features, or applying access controls.
How to proactively mitigate F5 BIG-IP vulnerabilities
Remediating vulnerabilities involves implementing several strategies and best practices to ensure the security of your F5 systems and the applications they support. Best practices focused on configuration, maintenance, and monitoring.
Here are some key recommendations:
Run regular software updates
- Keep software updated: Regularly update to the latest version of BIG-IP software to ensure you have the latest security patches and features.
- Subscribe to security advisories: Follow F5’s security advisories and apply relevant patches promptly.
Follow configuration best practice
- Harden administrative access: (use strong passwords for all accounts; implement multi-factor authentication (MFA); restrict administrative access to trusted IP addresses using ACLs; disable unused services and interfaces.
- Secure remote access: Use SSH with key-based authentication instead of password authentication for remote access. Disable SSH root login.
- Minimize attack surface: Disable any unused features and modules to reduce the potential attack surface.
- SSL/TLS best practices: Use strong ciphers and disable weak ones. Regularly update SSL certificates and ensure they use secure algorithms.
Harden network security
- Segregate management and data traffic: Use separate VLANs for management traffic and data traffic to ensure that management interfaces are not accessible from the data network.
- Network firewall policies: Apply strict firewall policies to restrict access to BIG-IP management interfaces.
Use logging and monitoring
- Enable Logging: Configure detailed logging for both traffic and administrative activities. Use a centralized logging system to aggregate and analyze logs.
- Monitor for Anomalies: Implement monitoring tools to detect unusual activity or potential security incidents.
Implement access controls
- Role-Based Access Control (RBAC): Implement RBAC to ensure users only have the permissions necessary for their role.
- Audit User Activity: Regularly review user access and activity logs.
Run regular backups and test your recovery plan
- Regular Backups: Schedule regular backups of your BIG-IP configurations and store them securely.
- Disaster Recovery Plan: Have a tested disaster recovery plan in place to quickly restore functionality in case of a failure or attack.
Enforce security policies and compliance
- Security Policies: Develop and enforce security policies that include the use of secure configurations, regular audits, and adherence to compliance requirements.
- Regular Audits: Conduct regular security audits and vulnerability assessments of your BIG-IP systems.
By following these recommendations and best practices, you can significantly enhance the security posture of your F5 BIG-IP systems and protect them against vulnerabilities and CVE exploitation attacks.
*F5 and BIG-IP are trademarks of F5, Inc. Loadbalancer.org has no affiliation with F5, Inc. so use of these names, trademarks and brands does not imply endorsement by either party.














