Load balancing Metaswitch EAS SSS

Useful resources
About Metaswitch
Metaswitch and Loadbalancer.org have a long-standing partnership for the implementation of EAS SSS. Whether deployed as hardware or virtualized, the Loadbalancer.org solution ensures EAS SSS is highly available and highly secure.
High Availability, Low Complexity – Unbreakable Load Balancer Solutions
Loadbalancer.org has a philosophy of working closely with business partners, such as Metaswitch, to provide simple to implement, highly available load balancing solutions. Loadbalancer.org works tirelessly to understand customer’s businesses – their systems, workflows and pain-points. Through this enhanced understanding Loadbalancer.org are able to provide easy to install, ultra-reliable, fully scalable load balancer applications. All supported by a dedicated team of technical professionals providing category-leading after-sales services.
Customized Security as Standard – Protecting You From Malicious Threats
The Loadbalancer.org appliance includes a fully integrated industry standard Web Application Firewall (WAF) by default. Although a wide number of 3rd party commercial hardware and virtual WAFs are currently available, these are typically not configured to meet the specific and ever-changing threats faced by communication service providers. Therefore, Metaswitch recommend that customers looking to enhance their network security upgrade to a Loadbalancer.org WAF Gateway.
Developed collaboratively with Metaswitch and based on real-world customer experience, the Loadbalancer.org solution explicitly addresses known threats in the Metaswitch installed base using five custom WAF rules specifically developed by Loadbalancer.org to protect a Metaswitch EAS DSS/SSS deployment.
Custom Rule Set Provides Explicit Protection for Metaswitch Customers:
- Rule 1 protects the CommPortal login page against denial-of-service (DoS) attacks.
- Rule 2 protects against repeated failed login attempts to CommPortal.
- Rule 3 protects the CommPortal login page against HTTP POST request-based DoS attacks.
- Rule 4 prevents username based abuse.
- Rule 5 prevents password-based abuse.
Each rule is tuneable to meet the needs of a specific Metaswitch EAS deployment. In busier environments that process significant amounts of traffic, the rules can be relaxed to allow for more requests against the CommPortal login page. The rules can also be tightened to be more aggressive, which may be appropriate in smaller deployments where only a handful of genuine failed customer logins would be expected over a given period of time.
Please see the below, ‘WAF Gateway with Metaswitch EAS DSS/SSS Deployment Guide’ and ‘Protection from Malicious Threats – Metaswitch advice’, for further details of the customised security solutions developed for Metaswitch.
Sizing, Capacity & Performance
In this environment, the EAS servers may also be connected to separate signalling and media networks. These additional networks carry SIP and RTP traffic respectively. It is not necessary to connect the load balancer to them as the load balancer is not responsible for load balancing SIP or RTP traffic.
For deployments up to 250,000 subscribers, your virtual host should be allocated a minimum of 8 vCPU’s, 16GB RAM and 8GB disk storage.
This specification will support the following bandwidth and connection thresholds:
| Source | Destination | Bandwidth | Packets | Concurrent connections |
| Internet | EAS | 100 Mbit/s | 70,000 pkts/s | 380,000 |
| EAS | Internet | 700 Mbit/s | 55,000 pkts/s | 380,000 |
For larger deployments, your Metaswitch support representative will give you details of the expected load on your load balancers based on your predicted usage profile.
How to load balance Metaswitch Virtual EAS SSS
There are two ways that Metaswitch Virtual EAS SSS can be deployed. The deployment type used determines how the load balancer must be configured. It is essential to know which type of deployment is in place or being planned before attempting to set up a load balancer. If the deployment type is not clear, please contact Metaswitch support for further information. Some of the virtual services needed to load balance Metaswitch Virtual EAS SSS require source IP persistence. The EAS servers include a file named pools.txt which describes the virtual services that need to be set up, whether or not they require persistence, and if so what persistence timeout value should be used.
In a virtualized environment, the Virtual EAS SSS deployment type used determines how the load balancer must be configured. It is essential to know which type of deployment is in place or being planned before attempting to set up a load balancer. In this scenario, the Loadbalancer.org solution should be used to provide both load balancing and protection against security vulnerabilities.
Hardware installs follow a significantly different deployment architecture, so it’s best to contact your Metaswitch support representative for assistance. In this scenario, a separate pair of dedicated Loadbalancer.org appliances should be installed to provide protection against security vulnerabilities.
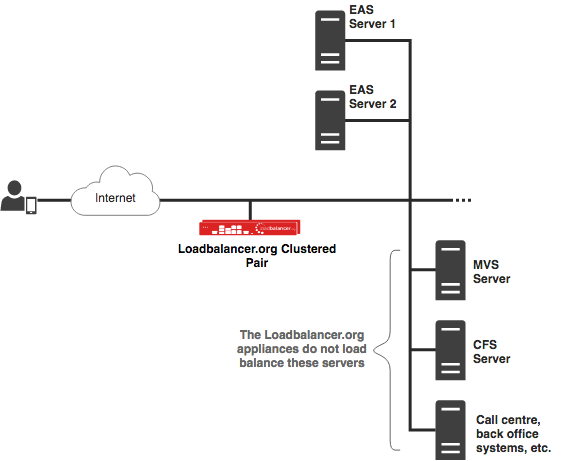
For other modes of implementation and additional details, please refer to the below Deployment Guide.
Testing & Verification
Metaswitch recommend using some specific tests which make use of the EAS Craft menu and the CommPortal web portal. These include Pool Configuration, Health Checking, Persistence & Failover / High-Availability. The System Overview in the Loadbalancer.org appliance can also be viewed in the WebUI. It shows a graphical view of all VIPs & RIPs (i.e. the EAS servers) and shows the state/health of each server as well as the state of each cluster as a whole. Please refer to the below Deployment Guide for full details.
guides

Metaswitch Virtual EAS SSS Deployment Guide
Read deployment guide
Metaswitch EAS WAF Gateway Deployment Guide
Read deployment guidecase study

LS Networks - Helping sustain 100% availability for Metaswitch platform
Read case studyother

Protection from malicious threats - Metaswitch advice
Read other
Metaswitch WAF explainer
Read other

